- The ransomware threat is showing no sign of abatement, with ransomware payment totals exceeding 1 billion USD for the first time in 2023.
- - These attacks are becoming more sophisticated, leveraging Ransomware-as-a-Service (RaaS) platforms to enable broader and more frequent attacks.
- - RaaS operates under a franchise system where a central syndicate develops ransomware tools and rents them out to affiliates who carry out the attacks. This model has lowered the entry barrier for cybercriminals and expanded the scale of attacks.
- - Groups like REvil, DarkSide, and LockBit have led some of the most disruptive ransomware campaigns, employing tactics like double-extortion, where they demand ransoms for decryption keys and to avoid data leaks.
- - Regular software updates, using a VPN download, and implementing strong authentication methods can fend off various types of attacks.
-
- In a ransomware attack, isolating the threat and avoiding ransom payments are recommended while notifying law enforcement.
Imagine starting your day with the shock of a frozen computer screen displaying nothing but a demand for payment. Last year, thousands experienced this nightmare as ransomware attacks surged, evolving into a relentless force threatening individuals and businesses. Ransomware is malware that encrypts digital files, holding them hostage until a ransom is paid. In 2023, 1 billion USD in ransom was paid, the highest amount ever.
Cybercriminals use increasingly sophisticated encryption methods, making it nearly impossible for victims to regain access without paying. Additionally, using cryptocurrencies allows attackers to receive payments anonymously, further complicating tracking and prosecution efforts. The scope of attacks has expanded from individual systems to crippling entire networks, including critical infrastructure and major corporations, resulting in significant financial and operational disruptions.
These incidents cause immediate financial damage and leave lasting scars on the reputations of affected organizations, eroding trust among customers and partners. Ransomware syndicates aren’t only targeting big players—they’re leveraging fear in everyone with access to a computer and bank account to profit from our dependence on technology. According to the 2024 Allianz Risk Barometer survey, the financial stakes are enormous with cyber risks now topping the list of global business concerns.
The economic impact of cybercrime is expected to reach 9.5 trillion USD by the end of this year and could increase to 10.5 trillion USD by 2025, driven by advancements in AI technology. At the heart of these attacks is the increasingly accessible market of Ransomware-as-a-Service (RaaS) platforms, available for as low as 40 USD.
But who are the people behind these operations? What drives someone to engage in high-stakes digital extortion? From thrill-seekers to politically motivated groups, the motivations behind these attacks are as diverse as the attackers themselves.
We spoke with ethical hackers and cybersecurity experts at ExpressVPN to delve into the dark world of ransomware. Join us as we explore the motivations, tactics, and significant impacts of the world’s most formidable ransomware syndicates.
Jump to...
The growing threat of ransomware attacks
What is ransomware-as-a-service?
The world's biggest ransomware attacks
The world's biggest ransomware groups
How and why are ransomware targets chosen?
Psychological tactics used by ransomware groups
The role of AI in ransomware attacks
Protect yourself from falling victim to ransomware
What to do if you’re a victim of ransomware
The growing threat of ransomware attacks
2023 marked the worst year on record for ransomware activities. With total ransom payments soaring to a staggering 1 billion USD, as tracked by Chainalysis, digital extortion saw a significant shift. The increase wasn't just in terms of money—CyberInt reported a dramatic 56% surge in ransomware incidents, tallying over 4,368 attacks. This data includes reports from news and ransomware gangs who often publicize their victims on dark web sites to pressure them by threatening to release stolen data.
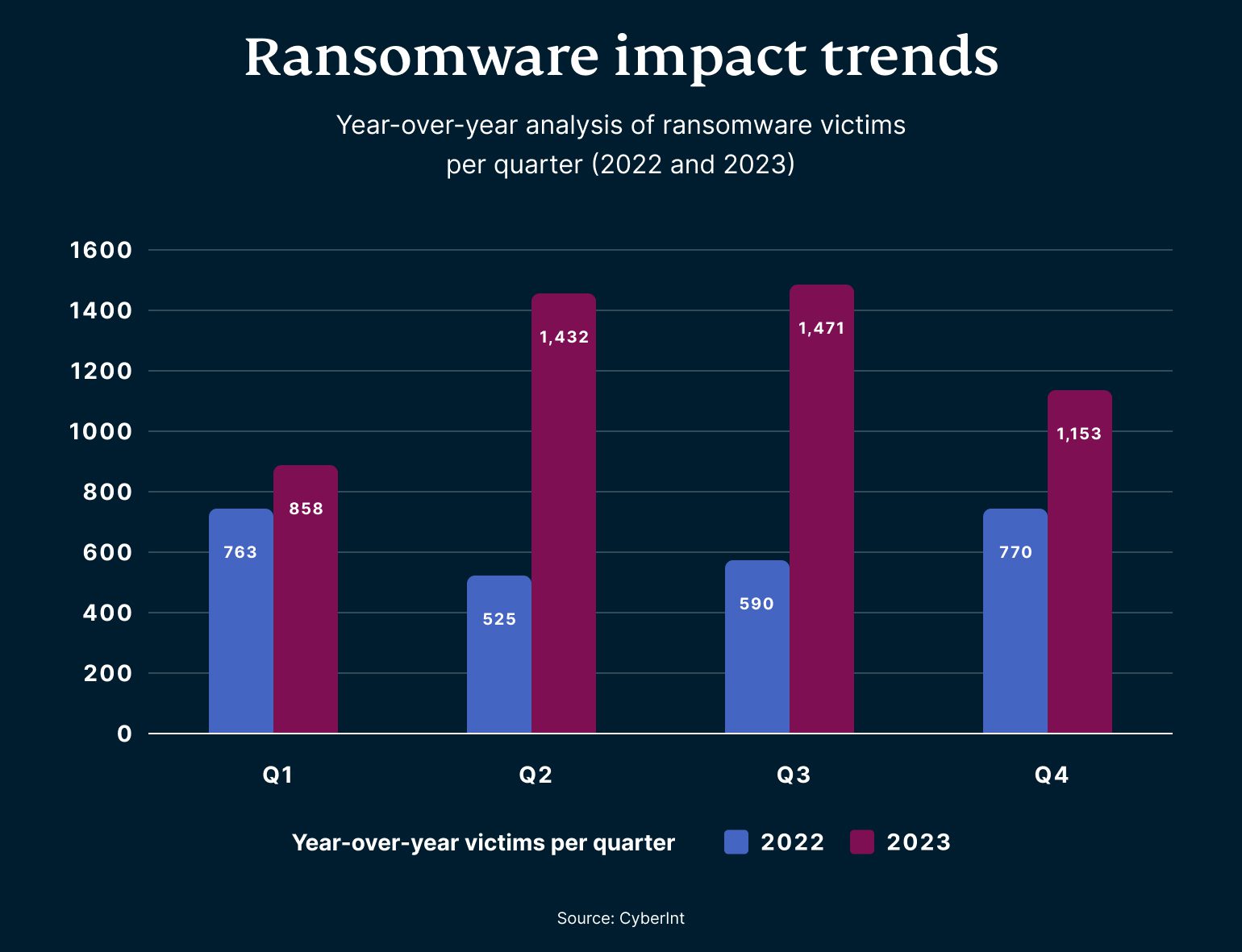
After a brief decline in 2022, when fewer ransoms were paid than the previous year, 2023 witnessed a strong comeback. Propelled by both seasoned hacking collectives and formidable newcomers, the total amount of ransomware payments tracked across blockchain networks reached a record-breaking high, nearly doubling from the previous year. This resurgence, driven in part by “big-game hunting”—ransomware operators targeting entities that can't afford to be crippled by attacks and are more likely to pay large ransoms—highlights a worrying trend. A Statista study further sheds light on the scale of the issue, noting a staggering 318 million ransomware attempts detected by organizations globally in 2023.
What is ransomware-as-a-service (RaaS)?
One significant factor behind this surge is the advent and accessibility of Ransomware-as-a-Service (RaaS). Operating much like a franchise, this model allows the central syndicate to develop ransomware tools and rent them out to affiliates who execute the attacks. This system has democratized high-stakes digital extortion, enabling anyone with the desire—and a minimal investment—to launch devastating cyberattacks.
“In the past, someone had to want to attack you and be capable of pulling that attack off themselves. Now they just need the desire and the financial means to acquire these services.”
Nathan Hartzell, a principal security architect at ExpressVPN, explains the profound impact of this shift: “In the past, someone had to want to attack you and be capable of pulling that attack off themselves. Now they just need the desire and the financial means to acquire these services.”
This collaborative approach not only increases the frequency of ransomware attacks but also enhances their reach and effectiveness, targeting victims ranging from private individuals to critical infrastructure entities. Affiliates deploy the ransomware, encrypting victims’ files and demanding a ransom for decryption, with the profits split with the RaaS provider, encouraging innovation and aggression in ransomware tactics.
Groups empowered by RaaS
The surge in RaaS has facilitated the rise of specialized ransomware groups, which utilize these platforms to execute their attacks, making cybercrime more accessible than ever. Catalin Oancea, a threat hunter and analyst at ExpressVPN, sheds light on the motivations and methods of various types of organizations enriched by RaaS:
1. Access seekers or initial access brokers: These groups specialize in identifying and exploiting vulnerabilities within a target's network. Ranging from advanced attackers to amateur hackers, they secure an initial foothold in a system, paving the way for ransomware deployment. Their strategies include phishing and brute force attacks on logins and servers.
2. Data brokers: Focused on stealing or acquiring personal information such as names, addresses, and social security numbers, data brokers sell this information on underground marketplaces. This stolen data can be used for various illegal activities, including identity theft and phishing scams, often in collaboration with initial access brokers to pinpoint potential victims.
3. Spy agencies: These groups diverge from financially motivated traditional ransomware groups. They use ransomware attacks to fulfill broader geopolitical objectives, such as disrupting the operations of a target country, highlighting the strategic use of ransomware in cyber warfare.
The different types of hackers utilizing RaaS
The RaaS model has not only simplified the process of launching ransomware attacks but also broadened the spectrum of individuals and groups involved in these activities. By lowering the technical barrier, RaaS has attracted a diverse array of hackers, each bringing their unique motives and methods to the table:
Black hat hackers
Black hat hackers engage in illegal activities such as financial data theft, ransomware deployment, or critical system disruption. By leveraging RaaS, they can execute more attacks with minimal effort, using tactics like countdown timers and data loss threats to extort payments from their victims.
White hat hackers
Also known as ethical hackers, these individuals use their skills to uncover and remedy system vulnerabilities. They often work for security firms or conduct authorized penetration tests, using tools similar to those found in RaaS to enhance system security.
Gray hat hackers
Gray hat hackers exploit security weaknesses without clear malicious intent. They may use RaaS tools to identify flaws and publicly disclose them, sometimes without notifying the affected organization, to push for quick remediation and raise security awareness.
Hacktivists
Hacktivists employ hacking for political or social activism, harming organizations as a form of protest. RaaS enables them to carry out disruptive cyberattacks that attract public attention to their causes.
Script kiddies
These are inexperienced hackers who use ready-made scripts or hacking tools to launch attacks. RaaS is attractive to them because it provides powerful capabilities without requiring advanced technical knowledge. They target known vulnerabilities in widely used systems.
Espionage hackers
These groups execute cyberattacks to advance their country's geopolitical interests. They often use RaaS for complex spy activities, targeting foreign governments, defense contractors, and major corporations to steal sensitive information or disrupt operations.
Hartzell also points out that these groups are driven by more than just profit. “These actors target industries, individuals, and governments aligned with their national objectives. Hacktivists go after their most despised industries, while script kiddies target whatever they believe they can exploit for notoriety.”
The world’s biggest ransomware attacks
A small business or even an individual can get hit by ransomware. But the ones that make headlines affect large organizations, disrupting essential services for numerous customers and sometimes coming with the threat of data leaks. They are also likely to ask for the largest payments.
That said, in the greater scheme of business costs, ransom demands tend to seem paltry—what’s a few million to a large corporation anyway? This reflects the attackers’ desire to get paid rather than face resistance. The losses to a company that refuses to pay are almost undoubtedly greater than the ransom itself.
Here are a few of the largest ransomware attacks:
| Victim | Attacker | What happened |
|---|---|---|
| Colonial Pipeline | Darkside | The attack in May 2021 crippled systems, preventing fuel from reaching customers. Colonial Pipeline paid a 5 million USD ransom within hours of the attack. The Justice Department was later able to seize 2.3 million of the crypto used to pay the ransom. |
| Costa Rica government | Conti | In April 2022, Conti launched a ransomware attack against Costa Rica, leading to significant delays in public administration and financial operations. The Costa Rican government declared a national emergency and defiantly refused to pay the 10 million USD ransom, which was increased to 20 million USD. The losses to Costa Rica was 30 million USD daily. |
| Impresa | Lapsus$ | In January 2022, Lapsus$ breached Impresa, a Portuguese media conglomerate, taking down several websites and TV channels. Lapsus$ leaked a vast amount of sensitive data online, including emails, contracts, and personal information of employees and customers. |
| Windows systems, notably UK’s National Health Service | Lazarus Group | The WannaCry ransomware attack in 2017 affected systems worldwide by exploiting vulnerabilities in Microsoft Windows. It impacted organizations such as the NHS in the UK, telecommunications companies, and various other businesses globally, causing widespread disruption and economic losses. |
The world’s biggest ransomware groups
Ransomware groups have become so sophisticated that they operate like companies, with reports of Conti, one of the largest, even having its own HR department. But ransomware groups can come and go quickly, often shutting down after an ultra-high-profile attack and morphing into a different organization. Sometimes international agencies work together to take down groups. That doesn’t stop new groups from cropping up.
So who are the major players these days, and what do they do? Here are some of the biggest groups right now.
1. BlackBasta
BlackBasta entered the ransomware scene in early 2022, believed to be spun off from Conti, which had attacked numerous big names and became a household name amid its attack on the Costa Rican government. What this means is members of BlackBasta had plenty of experience right off the bat.
BlackBasta’s debut has been anything but subtle. It quickly established a formidable reputation, primarily through their adoption of double extortion tactics. This strategy involves two forms of ransom: one for the decryption key to unlock the victim's data and another to prevent the release of the stolen data.
Last year, the group was allegedly responsible for extorting at least 107 million USD in Bitcoin and funneling the funds through the cryptocurrency exchange Garantex.
2. Blackcat (ALPHV)
BlackCat, also known by the aliases ALPHV or Noberus, surfaced in November 2021 and is said to be formed by former members of now-defunct Darkside, which notoriously attacked Colonial Pipeline. The group’s malware targets Windows and Linux systems. BlackCat is infamous for its triple-extortion strategy, which includes demanding a ransom to decrypt files, promising not to leak stolen data, and preventing distributed denial-of-service (DDoS) attacks.
According to the FBI, over 1,000 victims worldwide have been attacked by BlackCat. Operating under the RaaS model, it recruits affiliates through cybercrime forums. Noteworthy targets include OilTanking GmbH in January and Swissport in February earlier this year, where it captured 1.6TB of sensitive data, including internal communications and personal information. Despite Swissport's breach mitigation within two days, BlackCat marketed the stolen data, showcasing its double-extortion tactics.
3. Clop
Clop, also called Cl0p, is a prominent ransomware group known for its sophisticated, multilayered extortion schemes and widespread influence. The organization is notorious for deploying ransomware attacks that encrypt a victim’s data, typically adding the “.clop” extension to the encrypted files, marking their distinct footprint in the cybercrime arena. Their targets span various sectors, including financial institutions, critical infrastructure providers, healthcare organizations, large enterprises, and educational institutions.
Recently, the group allegedly exploited a zero-day vulnerability in Progress Software's MOVEit Transfer—a tool used for enterprise file transfer. Clop launched a widespread attack, stealing data from various organizations worldwide—including government, public, and business entities. Notable victims of the attack included the public school system in New York City and a UK-based HR solutions and payroll company, which has clients such as British Airways and BBC.
4. LockBit

(Credit: WikiCommons)
LockBit, established in 2019, has quickly become one of the most prominent ransomware groups in the world, having received more than 120 million USD in ransom payments.
Operating under a RaaS model, LockBit supplies sophisticated malware and attack infrastructure to its affiliates, who execute the attacks and share the profits. The group targets a wide range of sectors, including energy, manufacturing, government, healthcare, and education, underscoring the broad and serious threat they pose.
LockBit was dealt a major blow this year, with the U.S. and UK law enforcement agencies seizing websites that the group was using to coordinate and servers it was using for operations. Two people were also indicted. The group is likely no longer able to continue.
5. REvil
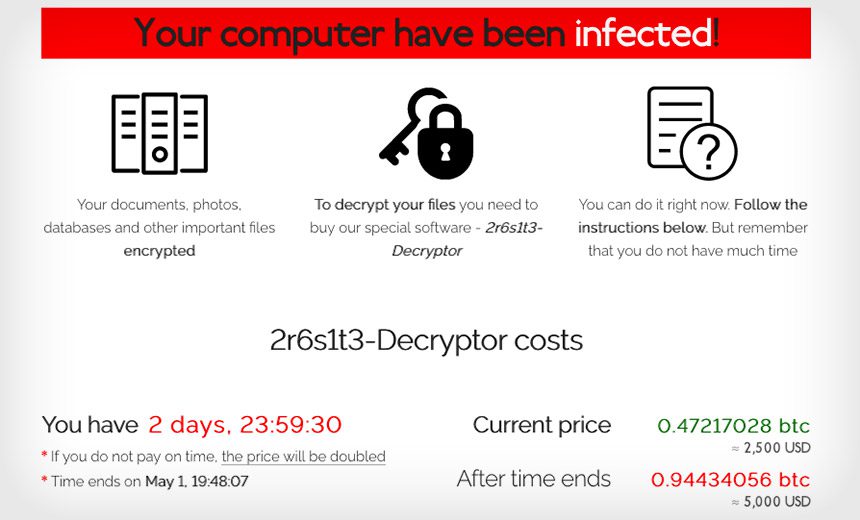
REvil, also known as the Sodinokibi ransomware group, operates under a RaaS model. This scheme involves creating and leasing out malicious software that encrypts victims' files. Affiliates use this ransomware to target both individuals and businesses, demanding payments to decrypt the data, with REvil taking a cut of the profits.
The group has gained notoriety for targeting high-profile victims like Apple. They also manage a dark web marketplace, Happy Blog, where they threaten to publish stolen data unless ransoms are paid. Despite international law enforcement efforts, including cooperation from Russia, to curb their activities in early 2022, the legacy and methods of REvil continue to pose a stark reminder of the dangers of RaaS and the ongoing threat of ransomware attacks.
How and why are ransomware targets chosen?
While anyone can fall victim to ransomware attacks, according to Hartzell, syndicates target those involved in significant business events like mergers or product launches. These periods are attractive due to the potential for reputational damage and stock price impacts, with preferred sectors including finance, healthcare, and critical infrastructure due to their operational significance. An FBI report highlights that attackers also strategically time their moves during business downtimes such as weekends and holidays to exploit reduced defensive activities.
“Wealthy individuals] become targets because their personal details, like email, Facebook, or Instagram accounts, are among the thousands or millions on a list purchased by hackers for use in automated attacks.”
However, the threat extends beyond corporations to individuals, particularly those with public profiles or substantial wealth. “More often, [wealthy individuals] become targets because their personal details, like email, Facebook, or Instagram accounts, are among the thousands or millions on a list purchased by hackers for use in automated attacks,” Hartzell explains.
This kind of direct extortion has been starkly demonstrated by incidents like the Vastaamo psychotherapy clinic breach in Finland. The clinic’s breach, initially in 2018 and again in 2019, resulted in the theft of tens of thousands of patient records containing highly sensitive information. By late 2020, the situation escalated as attackers started directly extorting both the clinic and its individual patients. They demanded substantial ransoms, about half a million dollars in Bitcoin from the clinic and approximately 240 USD from each patient, to prevent the public release of their private therapy sessions.
Psychological tactics used by ransomware groups
It’s clear that ransomware attacks disrupt systems and deeply impact the psychological state of their victims. Today, ransomware groups not only aim to paralyze systems but also to push victims to the point of desperation. Feeling cornered and overwhelmed, many feel that paying the ransom is their only escape.
Threatening to leak data on public shaming sites
Earlier this year, a deeply concerning trend emerged involving extortion schemes targeting teenage boys. In these sextortion scams, perpetrators threatened to release private images shared among the teens, even leading to a number of suicides. These cases starkly illustrate how threat actors are now leveraging public shaming tactics to coerce victims into paying ransom. This method involves cybercriminals threatening to expose personal information, such as financial records, intimate images, or private messages, on websites easily accessible online or through the dark web, unless a ransom is paid. This strategy exploits the fear of reputational damage and the potential legal consequences that come with the exposure of confidential information.
By leveraging public shaming sites, attackers create immense pressure on both individuals and organizations. The threat of having one's personal details exposed publicly can lead to significant emotional distress and prompt quick compliance with ransom demands to prevent further damage.
Virtual and physical intimidation
Ransomware groups are increasingly adopting other types of intimidation strategies to disorient and coerce their victims. By exploiting data pilfered during initial breaches, some attackers engage in direct harassment of employees through phone calls, emails, or even by commandeering company printers to churn out ransom demands. This direct approach creates panic and urgency. Additionally, using countdown timers intensifies this pressure by setting a strict deadline. If the ransom isn’t paid within this timeframe, the demanded amount may increase, or access to essential data could be permanently lost.
Social engineering
Social engineering is a deceptive technique used by cybercriminals to manipulate individuals into giving up confidential information or access to secure systems. This method exploits basic human behaviors—such as responding to urgent requests, the allure of free offers, or fear—by tricking victims into making security mistakes. Common tactics include:
- Phishing: Sending fake emails that appear to come from trusted sources to trick recipients into revealing personal information or clicking on malicious links.
- Baiting: Offering something enticing, like free gift cards, to lure victims into interacting with malware-laden files or links.
Once trust is established, attackers might ask the victim to click a link or download an attachment that infects their system with malware. Hartzell explains, “Social engineering exploits basic human tendencies—our responsiveness to urgent requests, greed, or fear. The most effective countermeasure is fostering a culture of skepticism.”
Targeted attacks
Cyber attackers are increasingly refining their strategies to make their campaigns more personalized and direct. This involves using the names of victims in phishing emails or ransom demands, which makes the threats seem more immediate. Such a personalized approach is designed to prompt quick action from the target.
The sophistication of these attacks has grown due to advancements in cybersecurity technology, such as enhanced email filtering, advanced antivirus programs, and machine learning tools.
Oancea explains the change in tactics. He says that, historically, cybercriminals would send millions of generic spam messages. "Now, due to improved detection technologies, these broad attacks are often stopped before they reach users. Today's syndicates are more likely to use targeted methods that are harder to detect and more pressing for the recipient."
The role of AI in ransomware attacks
Another significant part of cybercriminals personalizing their attacks is the integration of artificial intelligence (AI) in their strategies.
Enhanced phishing attacks
AI technology is enabling attackers to create more convincing and sophisticated phishing campaigns. By using deepfake technology, criminals can create and disseminate realistic audio and visual content. For example, in 2023, there was an incident where deepfake imagery of black smoke over the Pentagon caused temporary chaos and stock market drops.
Sophisticated vishing scams
Furthermore, AI plays an essential role in conducting vishing scams that are startingly authentic. These AI-generated phone calls mimic human voices with high accuracy, making the fake interactions seem real and trustworthy. This advanced technique goes beyond traditional phishing and spear-phishing, involving detailed interactions designed to trick the target into compromising their security.
Streamlining target identification
AI's ability to analyze vast datasets quickly also enhances the efficiency of cybercriminal operations. By automating the identification of potential targets, AI allows cybercriminals to focus their resources more effectively, reducing the time required to plan and execute attacks.
These developments in AI-assisted cyberattacks further emphasize the need for society to adopt a proactive and adaptive cybersecurity approach.
Protect yourself from falling victim to ransomware
As the scale and sophistication of ransomware attacks continue to escalate, safeguarding against these cyber threats becomes paramount. Studies, including the Thales Threat Report, consistently find that human error is the leading cause of data breaches. This underscores the importance of comprehensive cybersecurity training and robust technical defenses. Below, we explore some of the things you can do to strengthen your digital defenses and protect your data from ransomware threats:
Keep your software updated
Regularly updating your software closes security gaps and minimizes the risk of ransomware infections. Cybercriminals often exploit known vulnerabilities in outdated systems, so staying current is your first line of defense.
Use a VPN
A VPN download can bolster your digital security, especially on public Wi-Fi networks. While a VPN won't prevent you from falling victim to phishing or malware attacks, it encrypts your internet connection, shielding your data from cyber snoops and potential interceptors.
Use strong authentication processes
Implement robust authentication methods like multi-factor authentication (MFA) or two-factor authentication (2FA). These methods add a crucial layer of security, making it significantly harder for attackers to gain unauthorized access even if they have some of your credentials.
Maintain vigilance and healthy skepticism
Stay alert to the latest cyber threats and phishing tactics. Be skeptical of unexpected requests or messages, particularly those with links or attachments, and verify their authenticity before responding or clicking.
“No one will send you free money in an email, and your bank will not email you when there is a concern about money, explains Hartzell. “Banks will call you. Actual lawyers will tell you you have money coming from somewhere unexpected. Your ISP will not call you if they detect ‘bad traffic from your home router. If it sounds crazy or too good to be true, assume it is and challenge the source.”
Install trusted security software
Deploy comprehensive security solutions that offer real-time protection. Look for anti-malware and antivirus programs that continuously update their threat databases and provide robust monitoring tools to detect and block emerging threats.Use advanced security software.
Deploy comprehensive security solutions like Advanced Threat Protection (ATP), Endpoint Detection and Response (EDR), and Security Information and Event Management (SIEM) systems. These tools provide broader defense mechanisms than traditional antivirus software by detecting and responding to advanced threats.
Backup your data
Follow the 3-2-1 backup rule—maintain three copies of your data, store them on two different types of media, and keep one backup offsite. Regularly test your backups to ensure they can be restored quickly in case of an attack.
Regular training and simulated phishing tests
Educate yourself and your workforce on the latest cyber threats and defense strategies. Regular training sessions and simulated attacks can prepare you to better identify and respond to security threats in real-time.
Legal and compliance
Ensure compliance with relevant legal and regulatory frameworks for data protection. These not only help in safeguarding against liabilities but also enhance your overall cybersecurity posture.
What to do if you’re a victim of ransomware
Despite your best efforts to safeguard your data and systems, the unfortunate reality is that ransomware can still breach your defenses. This is often due to the sophisticated and ever-evolving tactics used by cybercriminals who exploit even the smallest vulnerabilities. Here’s a step-by-step guide on what to do if you find yourself in this stressful situation:
1. Isolate the threat quickly
The first step is to prevent the ransomware from spreading further. Disconnect the compromised device from all internet and local network connections, whether a computer or smartphone. If the infected device is part of a work network, inform your IT department immediately to initiate containment protocols.
2. Avoid paying the ransom
While it might seem like a quick fix, paying the ransom is risky, as there’s no assurance that you’ll regain access to your files. Succumbing to the attackers' demands only fuels the cycle of future ransomware attacks.
3. Assess your backup options
If you maintain regular, clean backups of your data, you may be able to restore your files without engaging with the attackers. This step underscores the importance of a consistent backup strategy as part of your cybersecurity best practices.
4. Report the Incident
Notify local law enforcement to report the cyberattack. They maintain records of such incidents and might offer assistance or guidance. Additionally, report the breach to any relevant cybersecurity services or directly to the platform involved, such as Apple or Microsoft, particularly if there is a risk that the attackers have obtained your payment information.
5. Conduct a malware scan
Employ reputable antivirus or anti-malware tools to thoroughly scan your device for remnants of ransomware and other malicious software. For extensive infections, consider consulting with a cybersecurity expert to ensure your device is thoroughly cleansed.
6. Update your security credentials
Change the passwords for all accounts accessed through the compromised device, emphasizing sensitive accounts like those for email and banking. It's also wise to enable multi-factor authentication where available.
FAQ: About ransomware groups
Who are the biggest ransomware groups?
Prominent Ransomware Groups as of May 2024
- REvil/Sodinokibi: Known for targeting large corporations and demanding substantial ransoms, REvil has been behind numerous high-profile attacks, including the infamous attack on JBS Foods in 2021.
- DarkSide: Gained notoriety for the Colonial Pipeline attack in May 2021, which led to significant fuel supply disruptions in the Eastern United States. They often use a "double extortion" tactic, where they encrypt victims' data and threaten to leak it if the ransom is not paid.
- Conti: An evolution of the Ryuk ransomware, Conti has been active since 2020 and is known for its rapid encryption process and large-scale operations targeting government agencies, healthcare, and emergency services.
- LockBit: Emerging in 2019, LockBit operates under a ransomware-as-a-service (RaaS) model, allowing affiliates to deploy the ransomware while the core developers take a cut of the profits. LockBit 2.0, their updated version, introduced automated encryption features that threaten to publish stolen data if ransoms are not paid.
Who are the people behind ransomware?
Key Characteristics of Individuals and Groups Involved in Ransomware Activities
The people behind ransomware operations are often part of organized cybercriminal groups. These groups can vary greatly in size and structure, ranging from small teams to large, sophisticated networks with dozens of members. Here are some key characteristics of the individuals and groups typically involved in ransomware activities:
- Cybercriminal syndicates: Many of the most prominent ransomware groups operate like professional organizations, with leaders, developers, negotiators, and affiliates. These syndicates are often based in countries with limited cybercrime enforcement and can operate with relative impunity.
- Hackers and developers: These are the individuals who create the ransomware code and update its functionalities. They are skilled in software development and often exploit vulnerabilities in software and networks to deploy ransomware.
- Affiliates: In ransomware-as-a-service (RaaS) models, the core developers of ransomware recruit affiliates who are responsible for spreading the malware. These affiliates typically receive a share of the ransom payments in return for their efforts in infecting systems.
- Money launderers and financial handlers: These operators manage the financial transactions and money laundering aspects of the ransom operation. Ransomware groups often demand payments in cryptocurrencies, which require expertise in managing and laundering digital currencies to avoid tracking and tracing.
- Insiders: Sometimes, insiders within organizations—employees, contractors, or other individuals with access—can facilitate ransomware attacks, either wittingly or unwittingly. They might provide access to systems or sensitive information that enables the deployment of ransomware.
- Technical support and negotiators: Some groups have members dedicated to negotiating ransom payments with victims, providing instructions on how to pay the ransom, and even offering technical support to victims in decrypting their data once the ransom is paid.
What are the three types of ransomware?
Types of Ransomware
The three main types of ransomware are:
- Encrypting ransomware: This type of ransomware encrypts files on the victim's system, making them inaccessible until a ransom is paid. The decryption key is typically held by the attackers, who demand payment in exchange for providing the key to unlock the files.
- Locker ransomware: Locker ransomware locks the victim out of their entire system, preventing access to files, applications, and sometimes even the operating system itself. Victims are usually presented with a message demanding payment to regain access to their system.
- Scareware: Scareware is a type of ransomware that uses social engineering tactics to trick victims into believing their computer is infected with malware or that they have committed a legal violation. The ransomware then prompts the victim to pay a fee to remove the supposed threat or avoid legal consequences.
Can you go to jail for ransomware?
Is it illegal to be a hacker?
Legality of Hacking
The legality of hacking largely depends on the hacker's motives and actions. In the cybersecurity world, hackers are classified into white and black hat hackers based on their intentions.
Legal Hacking
- White hat hackers: Also known as ethical hackers, these cybersecurity professionals use their skills to identify and fix system vulnerabilities with the system owner's permission. They aim to enhance security and protect data and infrastructure from malicious attacks, operating within legal and ethical frameworks.
- Penetration testing: Similar to ethical hacking, penetration testing is a sanctioned activity where security professionals simulate cyberattacks on a system to test its defenses. Companies often hire security firms to conduct penetration tests against their infrastructure.
- Research hacking: Researchers sometimes hack into systems to study malware, discover vulnerabilities, or develop security solutions. This type of hacking is usually done under strict ethical guidelines, often with permission from the system owners.
Illegal Hacking
- Black hat hackers: These hackers engage in illegal activities for personal or malicious gain, such as data theft, privacy violations, and system damage. Their actions, driven by motives like financial gain or espionage, often result in debilitating consequences for their victims, including financial loss and reputational damage.
- Grey hat hackers: Existing in a moral grey area between white and black hat hacking, they may identify and exploit vulnerabilities without permission but without malicious intent, sometimes even reporting the issues to the owners. However, the unauthorized nature of their activities can still lead to legal repercussions.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN