Is Bitly safe? What to know before clicking short links

Shortened URLs are everywhere, including on social media, in text messages, and across the web. Services like Bitly turn long web addresses into neat little links that are easy to share. But you might be wondering: is Bitly safe to use? Can you trust those shortened links, or are you at risk of clicking something dangerous?
In this article, we’ll tackle your concerns head-on. You’ll learn what Bitly is and how it works, the potential risks of clicking Bitly links (like malware or phishing scams), and the steps Bitly takes to protect users. Most importantly, we’ll share practical tips to stay safe when you encounter any short link.
💡Tip: Short links can track details about who clicks them, including your general location and IP address, which might feel like a privacy invasion. Using a VPN like ExpressVPN adds a layer of privacy by hiding your real IP and encrypting your connection. While a VPN won’t detect malware, it does prevent link trackers from pinpointing your location and can keep your browsing more anonymous. It’s a handy extra safeguard alongside the precautions we cover below.
What is Bitly?
Bitly launched in 2008 as a free site that compressed unwieldy web addresses into tidy snippets that fit a single tweet. The company has since grown into a multifeature link-management platform offering:
- URL shortening and branded domains (e.g., nyti.ms for The New York Times).
- QR code creation for print or product packaging.
- Mobile-optimized landing pages.
Bitly processes billions of redirects each month. It not only shortens links but also provides analytics: the person who created a Bitly link can see how many people clicked it, when they clicked, and sometimes from where.
Businesses using Bitly can lean on these analytics to see which social posts resonate, while individuals often use it for the cleaner look and character savings on apps with length limits.
How does a URL-shortening service work?
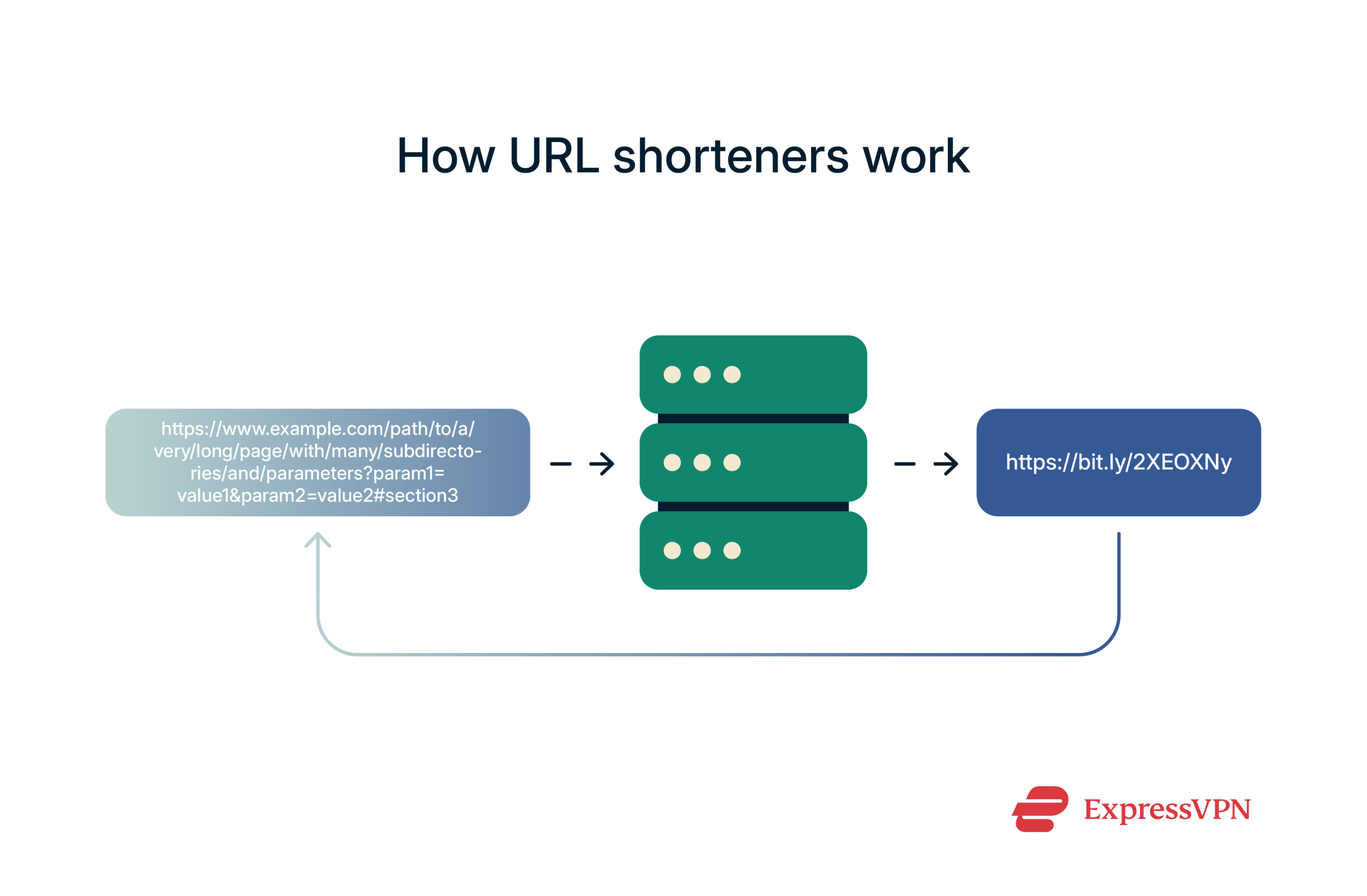 URL shorteners like Bitly work through a simple redirect mechanism. Here’s a quick rundown of what happens when you use Bitly:
URL shorteners like Bitly work through a simple redirect mechanism. Here’s a quick rundown of what happens when you use Bitly:
- You paste a long URL, say https://www.example.com/products/spring-sale-catalog?ref=newsletter-0429597, into Bitly’s input box.
- Bitly stores that URL in its database and assigns it a numeric ID, such as 2385162034.
- Because a numeric ID such as 2385162034 is still bulky, Bitly shrinks it with base-62 encoding. Base-62 is a way of representing numbers using 62 different symbols instead of the usual 10 digits we use in decimal. It uses 0-9, lowercase a-z, and uppercase A-Z, so the same number can now be expressed as 2bPtb0.
- Next, Bitly puts that short code after a domain:
- Default domain: If you use Bitly’s free option, the link becomes bit.ly/2bPtb0.
- Branded domain: Paid plans let you substitute a domain you own (say, nyti.ms for The New York Times). Bitly can then serve you links such as nyti.ms/2bPtb0 or a custom alias like nyti.ms/SummerSale.
When someone clicks the short link, Bitly
- Translates the ID back to the original number.
- Looks up the long URL.
- Records the click for analytics.
- Issues a 301 redirect to the target site. This is a permanent redirect; once a Bitly link is created, it’s not meant to be changed or reused. That said, Bitly lets you retarget a short link (meaning you can swap in a new destination URL) if the link sits on a domain you control (your branded domain) or on a Bitly Link‑in‑Bio page.
This instant redirect hides the destination until the browser arrives. This is an advantage for marketers, because it means they can clean up messy URLs and track engagement without distracting you with long web addresses. They can also test different landing pages behind the same branded short link without having to change the visible URL.
However, this invisibility is also a gift for cybercriminals. They can disguise harmful or misleading destinations behind a harmless-looking short link, tricking you into clicking without suspicion.
Why Bitly links can be risky
Bitly itself is a legitimate service; the company isn’t out to harm you. But bad actors can abuse any URL-shortening service, and Bitly is no exception. When you see a Bitly link, you often have no idea where it will actually take you until you click it. This is because shortened URLs cloak their endpoints, letting bad actors guide victims to malware, phishing pages, or “consent” prompts that install unwanted software.
Bitly doesn’t automatically sanitize or vet every single link at creation; otherwise, it would be hard to use the service freely. Instead, it relies on reactive measures and automated scanners to catch bad links.
This means some malicious links can slip through and be active at least for a time. If you click one of those before it’s caught, you could land on a dangerous site. Bitly acknowledges this, stating that it will block a link if it’s flagged as suspect or known to be malicious, but until a particular link is flagged, it may function normally.
Reports of malware spread via Bitly
One big risk with shortened links is that they might lead to malware.
Research has linked ransomware loaders, including Azorult and RevengerAT, to Bitly redirect chains. Attackers hosted the actual malicious files on disposable domains, then hid those domains behind Bitly to dodge email and social media filters. If you clicked on the link, you either saw a spoofed “software update” prompt or a blank 404 page while a background script downloaded the payload.
Even mobile ad-fraud rings joined in: a 2023 investigation uncovered Android trojans delivered through Bitly URLs embedded in fake giveaway texts. The redirect first led to a seemingly harmless content delivery network, then silently fetched and downloaded the malicious APK file.
Phishing attacks using short links
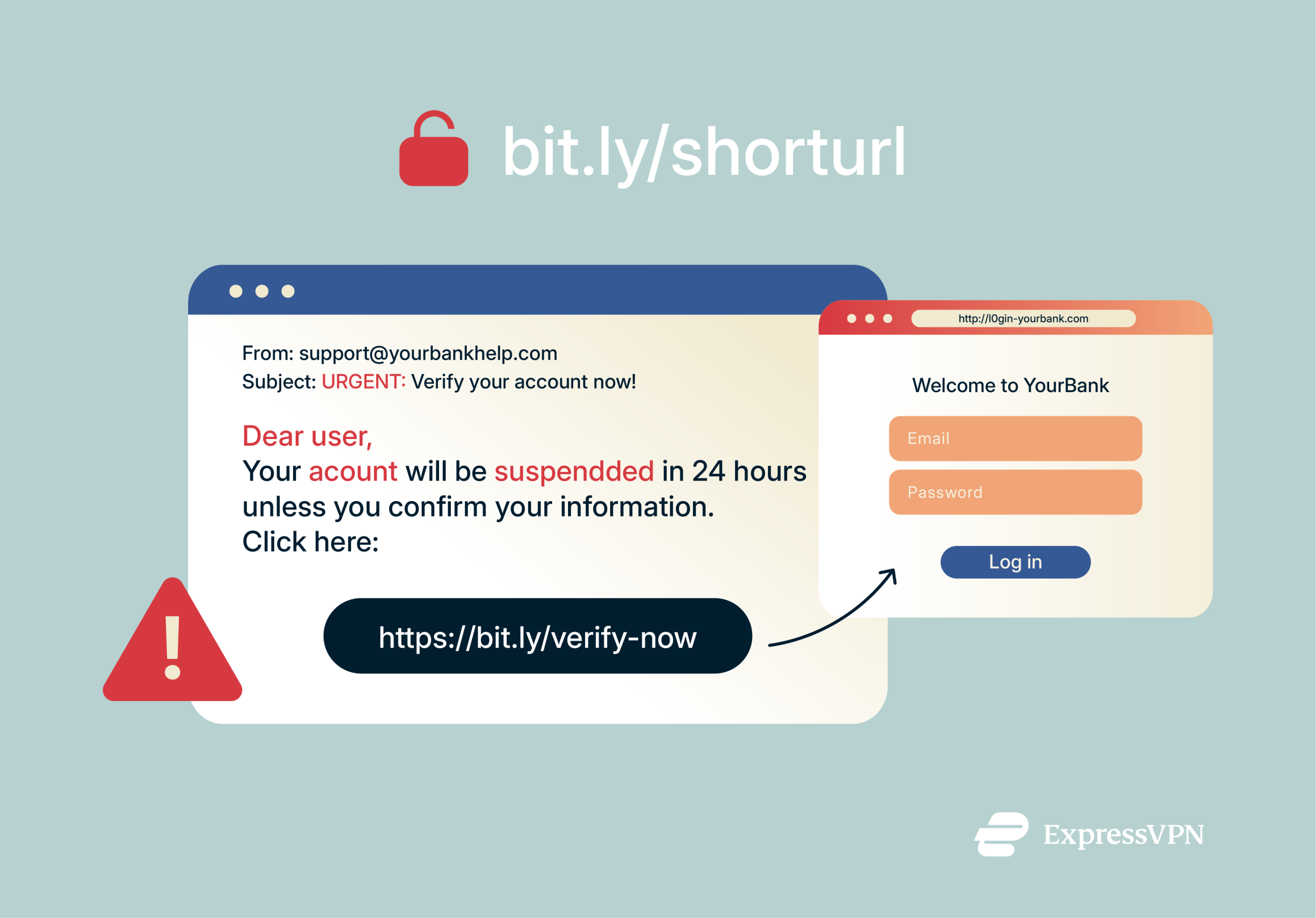 Phishing is another threat associated with Bitly links. Phishers love using short links in phishing attacks because they mask the true URL of their fake sites. Normally, one giveaway of a phishing site is that the URL looks odd; maybe one letter off from the real site or a completely unrelated domain. But if the attacker uses a bit.ly link, you can’t see that odd URL upfront. The Bitly link might appear as random letters, giving no hint of the phony website it hides.
Phishing is another threat associated with Bitly links. Phishers love using short links in phishing attacks because they mask the true URL of their fake sites. Normally, one giveaway of a phishing site is that the URL looks odd; maybe one letter off from the real site or a completely unrelated domain. But if the attacker uses a bit.ly link, you can’t see that odd URL upfront. The Bitly link might appear as random letters, giving no hint of the phony website it hides.
Short links also defeat the “hover to preview” defense on mobile, where status bars are hidden by default. Attackers exploit that blindness by timing SMS campaigns for weekends; click rates soar when users aren’t at their desks.
Bitly is aware of this misuse. Its system will investigate and block links that appear to be forgeries of other websites (in other words, phishing pages impersonating real sites). If you click a Bitly link that Bitly knows is phishing, you’ll see a warning page instead of the site. But again, this depends on Bitly detecting it or someone reporting it. New Bitly phishing links might not be flagged yet.
How attackers spoof Bitly links to mislead users
Aside from using genuine Bitly links for malicious purposes, attackers might also spoof Bitly links. Here are some of the tactics they use:
| Tactic | How it fools you | How to spot it |
| Lookalike domains (bitlly.com, bìt.ly) | Unicode accents or doubled letters pass a quick glance | Copy the URL into a plain-text editor; Unicode impostors stand out |
| Nested redirects | Bitly link → hacked site → hidden malware server (CDN), making detection harder. | Browser extensions such as Redirect Path reveal multi-hop chains |
| Fake hyperlink text | An email could say, “Please verify your account: bit.ly/Login-Help,” but if you hover over that hyperlink, you might see it actually goes to http://evilwebsite.ru/stealyourinfo | Always hover over hyperlinks and inspect the URL |
| Branded short domains | Attackers mimic a firm’s vanity domain (shopnow.link) by registering something similar (shopn0w.link) | Check the public WHOIS record; mismatched registration dates raise flags |
| Time-bomb links | The link is benign during scanners’ first crawl, then swaps destinations | Re-scan it with a security tool like VirusTotal before you share. |
How Bitly protects users
By now, we’ve painted a picture of the risks: malware, phishing, and deception via short links. The good news is that Bitly is not sitting idly by. Bitly acknowledges these risks and invests in multiple layers of defense.
Web Risk partnership with Google
One of the key ways Bitly tackles malicious links is by using Google’s Web Risk (Safe Browsing) database. It’s a constantly updated list of websites known to be phishing, hosting malware, or otherwise harmful.
Many browsers use Google’s list to warn users if they try to visit a dangerous site. Bitly uses a similar approach for its shortened URLs.
In practice, when a Bitly link is created or clicked, Bitly’s systems can check the destination URL against databases of known malicious sites. If these sources flag the destination, Bitly can block the short link from redirecting and show a warning instead.
Security measures and link scanning
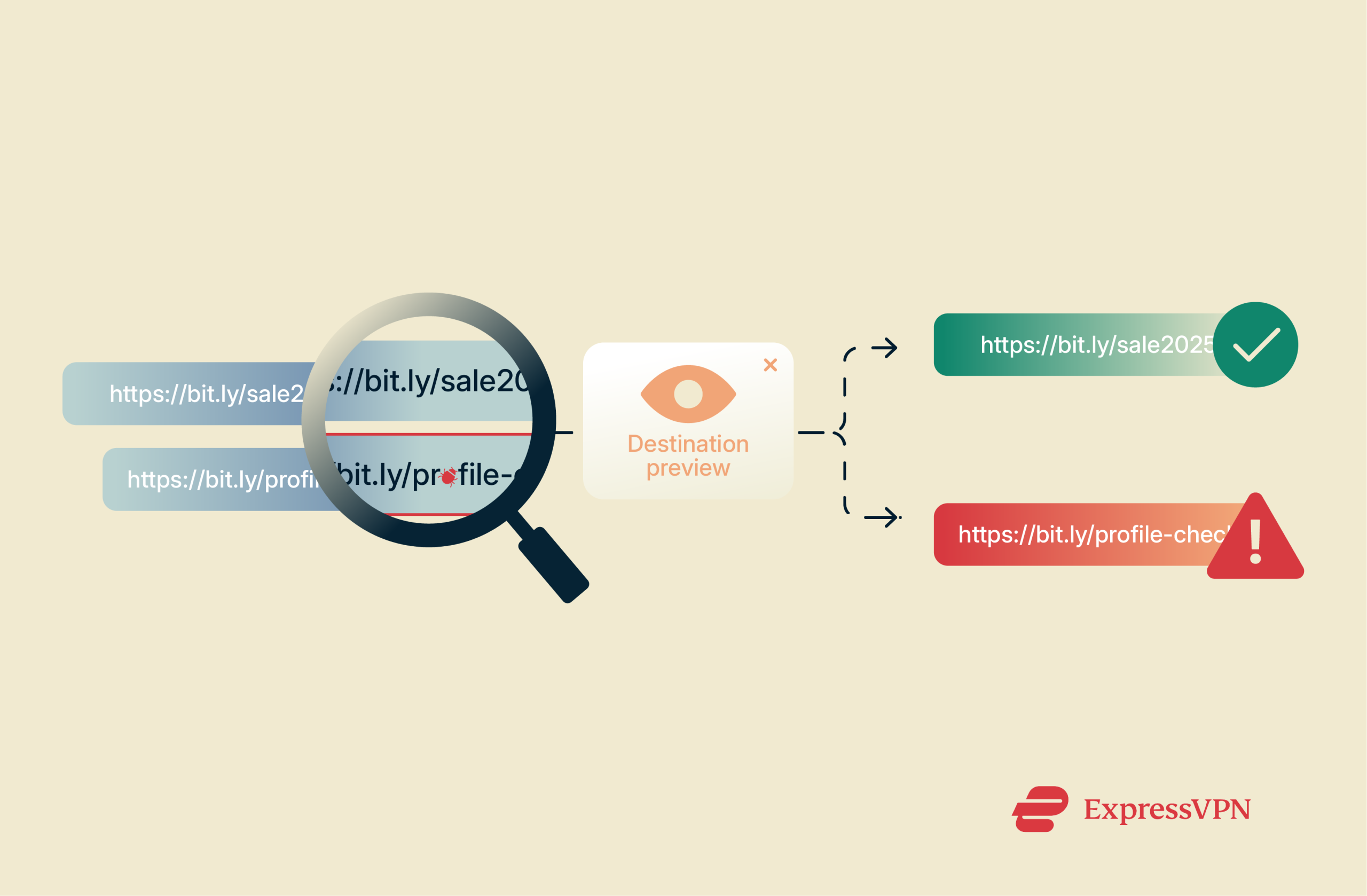 Bitly’s internal abuse prevention system combines:
Bitly’s internal abuse prevention system combines:
- Automated link scanning: Every new Bitly URL is run through antimalware engines and Safe Browsing APIs, blocking redirects to sites serving ransomware, drive-by exploits, or forced downloads before they reach users.
- Heuristic and behavior analysis: Bitly flags suspicious patterns such as mass link generation from the same account or large bursts pointing to newly registered domains, then automatically quarantines or disables those links pending review.
- Blocklists and user reports: The service ingests threat intelligence feeds and honors community abuse reports, instantly deactivating links that appear on phishing, spam, or malware blocklists and notifying creators when their links are taken down.
- HTTPS everywhere: All Bitly links resolve over Transport Layer Security (TLS). TLS encrypts the connection when a Bitly link redirects, preventing man-in-the-middle tampering during the redirect and ensuring attackers on open Wi-Fi can’t hijack or rewrite a click on its way to the destination.
- Warning interstitials: If a destination is later flagged as unsafe, Bitly replaces the redirect with a full-screen alert that explains the threat and advises users to close the page, effectively preventing accidental malware installations or credential theft.
- Partnerships with NGOs and safety organizations: Collaborations with Google Web Risk, the Anti-Phishing Working Group, and child-safety groups feed Bitly fresh intelligence on phishing campaigns, child sexual abuse materials, and extremist content, enhancing automated detection and takedown speed.
- Continuous improvement: Post-incident reviews feed straight back into detection rules, so each novel abuse technique Bitly encounters tightens future defenses and reduces attackers’ dwell time across the platform.
Since early 2025, Bitly has added a preview page feature. When someone clicks a free Bitly link, they’re first taken to a branded preview screen that shows the real destination, some basic analytics, and a small ad. This extra step gives users a chance to review the link before proceeding. It also allows Bitly to display a warning if the destination is later flagged as phishing or malware.
Bitly’s response to past incidents
Bitly has faced two main security challenges: a platform breach and abuse of its links in large-scale phishing campaigns. How it handled each one shows how seriously the company treats user trust.
In the 2014 database breach, attackers obtained off-site backup credentials, exposing users’ email addresses, hashed passwords, API keys, and social media tokens. With the combination of email addresses and hashed passwords, attackers can target users with phishing scams and attempt credential stuffing attacks on other websites.
The theft of API keys and social media tokens gives attackers potential unauthorized access to linked third-party services, compounding the potential damage beyond just the initially breached platform. Bitly responded within hours. It publicly disclosed the incident, revoked every exposed token, forced account password resets, and advised users to regenerate API keys.
Internally, it rolled out mandatory two-factor authentication for employees, re-encrypted sensitive data, and tightened access controls. No follow-on misuse of customer accounts was ever confirmed, and Bitly has had no reported breaches since.
Link abuse, on the other hand, remains an issue. Security researchers have traced several phishing waves, most notably during the 2016 U.S. election cycle, to Bitly links that redirected victims to spoofed login pages.
Although Bitly’s infrastructure wasn’t compromised, the company treated the misuse as a platform safety failure. It expanded automated scanning, began ingesting real-time threat feeds, and added a public abuse reporting form that promises a human review in under 24 hours. Bitly also started blocking redirect chains (one short link hiding another) to stop attackers from layering multiple shorteners to evade detection.
Throughout each event, Bitly emphasized transparency: blog posts, email notifications, and a detailed Trust Center FAQ explained what happened, which fixes went live, and how users could protect themselves. More recently, Bitly also started publishing a quarterly Transparency Report that discloses metrics on abuse reports, takedown speed, and false-positive rates, allowing outside scrutiny.
How to stay safe when using Bitly links
Bitly has some good security measures, but no automated system catches all threats all of the time. You should adopt safe browsing habits, especially when short links are involved. The great thing is that you don’t need to avoid Bitly or short URLs entirely; you just need to handle them smartly. Here are some tips and best practices to stay safe when clicking (or sharing) Bitly links.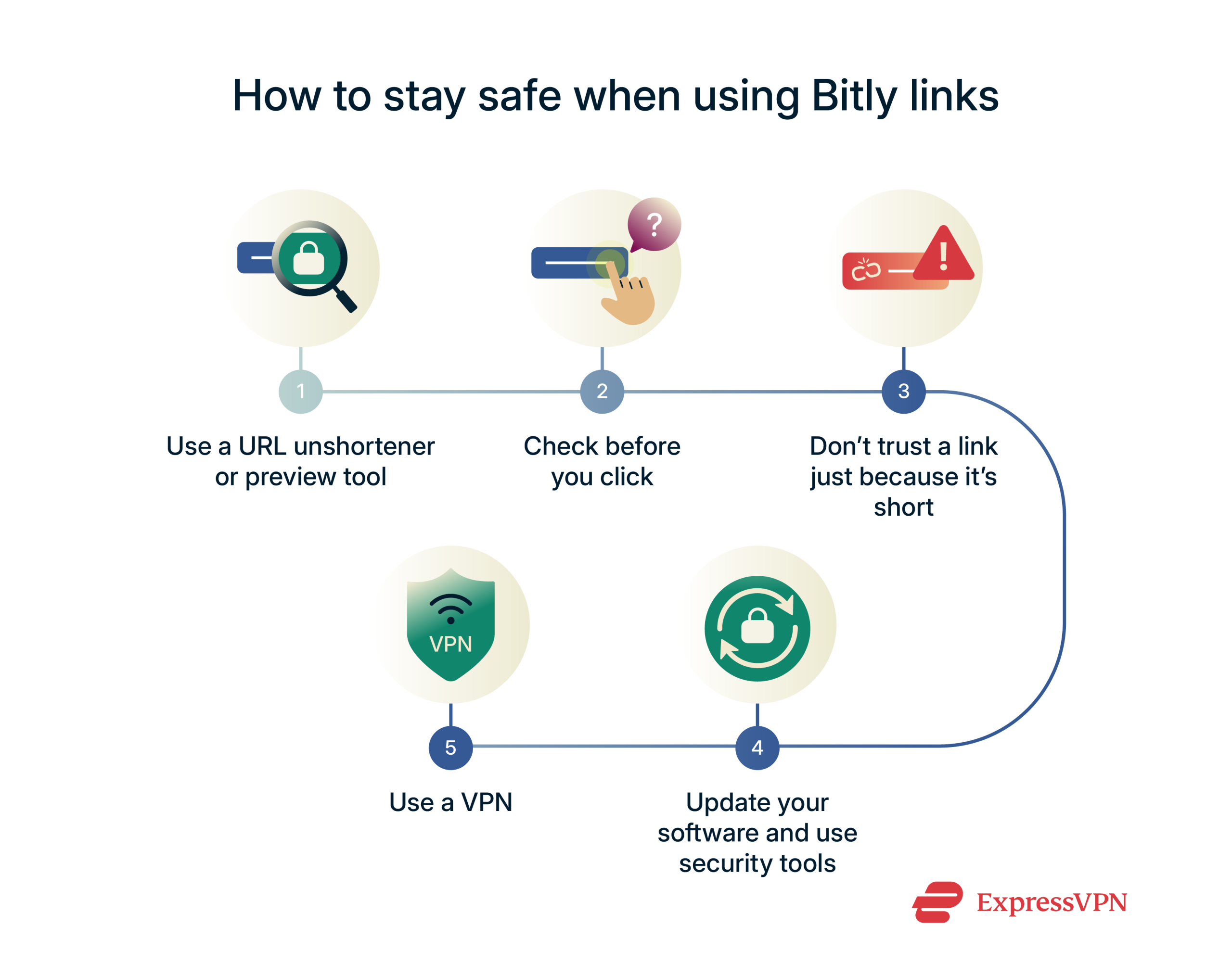
1. Use a URL unshortener or preview tool
One of the simplest ways to deal with the uncertainty of a short link is to expand it before you click it. There are many free tools available that let you do this safely:
- Bitly preview: Add a plus sign (bit.ly/ExampleLink+) to open a stats page that lists the full destination, HTTPS status, and first-seen date.
- Third-party expanders: Sites like CheckShortURL.com reveal redirect chains for dozens of shortener domains.
- Security extensions: Link Peek (Firefox) and Unshorten.link (Chrome) show the real link when you hover.
The key benefit of unshortening a URL is that you get to see where you would be headed without actually going there. If the expanded URL is something you don’t recognize or looks sketchy (e.g., malwaredownloads.ru or a random IP address or a misleading domain like secure-l0gin-support.net), you just saved yourself from a bad time because you can decide not to proceed.
2. Check before you click
This tip sounds simple, but it encompasses a few smart behaviors:
- Verify the context: Did your bank ever use Bitly before? If not, log in by typing the bank’s .com address instead.
- Hover or long-press: On desktop, the status bar shows the end of the short link, which is called the slug. This is a unique code that identifies the destination; on iOS and Android, a long press lets you preview where the link goes.
- Run a quick scan: Paste the link into Google Transparency Report or VirusTotal to check it; both pull from Safe Browsing and dozens of antivirus engines.
- Check the link’s text for clues: Sometimes even the short code or custom alias in a Bitly link can give you a hint about where it leads. Attackers often use enticing or attention-grabbing words (like “FREE” or “Giveaway”) to increase clicks. So if the link text matches the message but feels too good to be true, that’s a red flag.
3. Don’t trust a link just because it’s short
This point bears repeating: a short link is not inherently safe or safer than a long link. Sometimes people might think, “Oh, it’s a bit.ly link, and Bitly is a well-known company, so it must be okay.” Unfortunately, that’s not a valid assumption. Bitly is well-known, but anyone can create a Bitly link. It’s like a knife: a useful tool, but dangerous in the wrong hands.
So, treat a Bitly link with the same caution you would treat any unknown URL. In fact, treat it with more caution, because you lack visibility of what it is. Don’t let the clean, short appearance lull you into a false sense of security.
4. Update your software and use security tools
Even if you're careful about which links you click, malware can still exploit outdated software. Make sure your browser, operating system, and apps are regularly updated; security patches close known vulnerabilities that attackers often target.
Pair this with reputable antivirus or anti-malware tools that can detect and block threats if you accidentally land on a harmful site. Many of these tools work in real time and can stop malicious downloads before they cause damage.
5. Use a VPN
Even if a short link looks safe, your personal data can still be exposed, especially if you use unsecured public Wi-Fi. That’s where a VPN comes in handy. ExpressVPN helps protect your privacy by encrypting your internet traffic, preventing snoops or attackers on the same network from seeing where you go online.
It also includes a built-in tool, Threat Manager, which blocks known trackers and prevents your device from connecting to malicious domains flagged by trusted sources like Google Web Risk. This added layer helps shield you from drive-by malware, which can be triggered without your knowledge simply by clicking a compromised link.
What if you clicked a malicious Bitly link?
If you’ve already clicked a suspicious Bitly link, don’t panic, but act fast to limit the damage:
- Disconnect from the internet: Cut Wi-Fi or unplug your Ethernet cable immediately to stop any potential data theft and prevent further unauthorized access to your system.
- Run a full malware scan: Use a trusted antivirus or anti-malware tool to check for and remove threats.
- Change your passwords: Focus on accounts you accessed recently, especially if you entered any login details after clicking the link.
- Monitor your accounts: Watch for unusual activity, such as unfamiliar charges or login alerts.
- Report the link: Bitly has an abuse report form where you can flag dangerous links. This helps stop others from falling into the same trap.
Quick action can go a long way toward protecting your data, and reporting the threat helps keep others safe too.
FAQ: Common questions about Bitly
Can Bitly links contain malware?
How can I preview a Bitly link and check that it’s safe?
Are short links more dangerous than regular ones?
Is Bitly safer than other URL shorteners?
Is it safe to use Bitly?
Does Bitly sell data?
Is Bitly a good company?
What should I do if I click a malicious Bitly link?
- Disconnect from the internet. Cut the Wi-Fi or pull the Ethernet cable.
- Run a full malware scan. Use updated antivirus software.
- Change passwords. Focus on accounts you accessed recently.
- Monitor financial activity. Look for unusual logins or charges.
- Report the link. Bitly’s abuse form helps others avoid the same trap.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN