-

ExpressVPN joins forces with the Brooklyn Nets as an Official Digital Privacy Partner
ExpressVPN has announced a new partnership with the NBA’s Brooklyn Nets, joining the team as an Official Digital Privacy Partner. The collaboration has two main components: first, brand integratio...
-

How can you protect your home computer?
Many people underestimate how vulnerable their personal computers are. Without corporate-grade defenses or IT oversight, home setups are often easy targets. At the same time, new trends such as malwar...
-

What is Virtual Network Computing (VNC)? A complete guide
Virtual Network Computing (VNC) is one of the simplest ways to view and control another computer’s desktop over a network, giving IT teams, engineers, and everyday users direct access without being ...
-

Security concerns in cloud computing and how to address them
Cloud computing has transformed how organizations store data, build software, and manage everyday operations. It offers unmatched flexibility and scalability compared to traditional on-premises system...
-
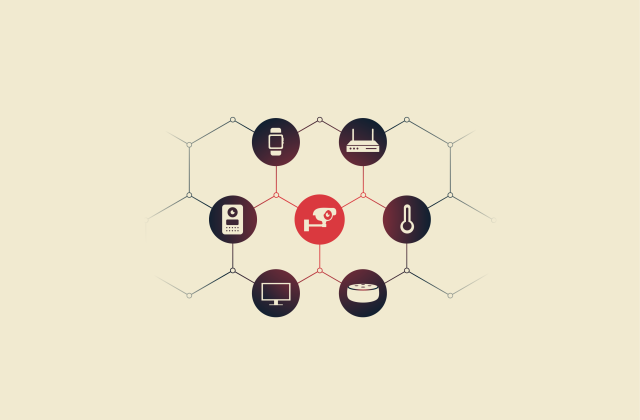
IoT vulnerabilities: How to identify and secure connected devices
All internet-enabled devices are at risk of being hacked into and exploited, but Internet of Things (IoT) devices tend to have weaker standards of security compared to the likes of computers and smart...
-

How to clear Instagram cache on iPhone, Android, and desktop
Instagram can sometimes slow down, with feeds, Stories, or Reels taking longer to load. When this happens, clearing the app’s cache is one of the simplest fixes. This guide explains how to clear Ins...
-

What is clickjacking and how to prevent it
You click “Continue” on what looks like the next step of a signup form. Nothing seems to happen, at least not until you notice a small charge tied to one of your accounts. That’s clickjacking in...
-

Hinge scams: Protect yourself from fake profiles
Not every match on Hinge is genuine. Cybercriminals create fake profiles on the platform to exploit trust and emotion. Such scams can have a significant impact on finances and overall wellbeing. This ...
-

What is a data warehouse? A complete guide for secure data management
Data warehouses are the backbone of modern analytics. They store large amounts of structured data from various sources, allowing organizations to analyze information, identify trends, and make data-dr...
-

Network configuration management for secure and optimized networks
A single misconfiguration can bring down an entire network. It might block someone from logging in, expose private data, or break secure VPN tunnels between offices. Yet, with so many devices and sett...
Featured




