How data breaches shaped the way we use passwords today

Every year, World Password Day nudges us to tighten up our digital defenses. Initiated to raise awareness about the role passwords play in safeguarding our private information, this day also serves as a reminder of our ongoing battle against cyber threats.
But why do we lean so heavily on passwords, and why do they need to be so complex? As World Password Day approaches on May 2, we explore the history of password security, tracing its origins back to the earliest days of digital authentication. We’ll uncover how major data breaches have not only exposed vulnerabilities but have also catalyzed significant changes in the strategies we use to manage and secure our passwords.
From simple strings of characters to today’s robust multi-factor authentication systems, join us as we explore the innovations that have shaped how we protect our digital lives today.
Jump to…
What were the first passwords?
Major data breaches: A timeline
The evolution of digital passwords
Best practices for password management
The rise of passwordless authentication
What were the first passwords?
Long before the dawn of the internet and the digital convenience we now take for granted, passwords were already a part of society’s security measures.
Ancient times
Tracing back to the times of ancient civilizations, passwords played an important role in maintaining confidentiality and securing communications. Roman military practices, for example, utilized “watchwords” to manage access through secured zones, ensuring that only those with the correct phrases could pass—effectively distinguishing friend from foe.
Cryptographic contributions (14th-17th century)
The medieval period marked significant advancements in the complexity of passwords with the rise of cryptography. In the 14th century, the Egyptian scholar Ahmad al-Qalqashandi's writings on cryptology laid down fundamental concepts that transformed secure communication. During the Renaissance, innovators like Leon Battista Alberti propelled these ideas further, developing polyalphabetic ciphers that enhanced the security of messages, setting the stage for the sophisticated encryption techniques we use today.
Read more: How encryption has shaped history and will define the future
Seals and signatures (19th century)
In the 19th century, officials used physical measures like wax seals on important decrees and letters to demonstrate authenticity. Like passwords, they provided assurance of identity. Of course, one main difference is they were not kept secret but rather were valued for their uniqueness, as their intricacies made them difficult to reproduce. In that sense, perhaps they can be compared to biometrics like fingerprints.
Speakeasies and secret codes (1920s)
During the Roaring Twenties in the U.S., the Prohibition era saw passwords assume a secretive role within the underground speakeasy scene. Access to these hidden bars required a whispered password, ensuring that only trusted individuals could take part in the covert nightlife, reflecting the passwords’ role in controlling access to restricted activities.
Military use of passwords (1940s)
During World War 2, particularly during the Battle of Normandy, military use of passwords evolved to include a password and a counter password system. This system was essential in verifying identities under the stress of wartime conditions, with famous instances like the use of a device known as a “cricket” in place of a password system by American paratroopers during D-Day serving as unique, temporary methods of identification.
The dawn of the digital password (1960s)
The transition to digital passwords occurred in the 1960s with the development of the Compatible Time-Sharing System (CTSS) by Fernando Corbató at MIT. It was born out of necessity with the advent of early computer systems. This innovation introduced password-protected user accounts, enabling multiple users to securely share system resources—an essential step towards the data privacy and security protocols we have today.
Network security and the digital age (1970s-2000s)
As technology progressed through the 1970s and 1980s, the widespread adoption of passwords became essential for accessing resources in multi-user systems and networks like the ARPANET, the precursor to the internet. This necessity expanded in the 1990s and 2000s with the internet's rise, establishing passwords as a fundamental component of digital security—crucial for protecting everything from email accounts to online banking.
However, as security measures like passwords evolved, so did the tactics of cybercriminals attempting to steal or bypass them.
How 10 major data breaches influenced password security practices
Data breaches across the globe have had a profound impact on how we handle our digital keys. Here’s a closer look at how some of the biggest breaches in history have transformed the way we manage password security:
1. TRW (1984)
Known as the first major data breach in history, the credit reporting agency TRW Information Systems (now Experian) experienced a significant incident in 1984 when a credit file password was stolen from a Sears store in Sacramento, California. This password allowed unauthorized access to the credit histories of approximately 90 million people. The stolen password was then posted on an electronic bulletin board, accessible to a wide audience for over a month before the breach was noticed and reported. The breach led to the exposure of sensitive data including names, addresses, social security numbers, and credit scores.
Response
The TRW breach led to major changes in how passwords and data security were managed, marking a shift towards more complex digital keys. It also influenced the development of stricter computer crime laws, including the Computer Fraud and Abuse Act of 1986, which strengthened legal protections against unauthorized computer and network access. This event catalyzed the cybersecurity industry, enhancing awareness about the risks of inadequate password management and data protection.
2. Yahoo (2013 and 2014)
The Yahoo data breaches affected nearly all user accounts across two separate incidents. Known as the most significant data breach in history, the 2013 breach affected every single Yahoo account—all 3 billion of them. The data included names, email addresses, telephone numbers, dates of birth, hashed passwords, and in some cases, security questions and answers. The 2014 breach compromised around 500 million accounts with similar personal data exposed. These breaches were significant not only because of their scale but also because of the nature of the data stolen, which directly impacted the security of the affected accounts. They also notably impacted Yahoo's valuation during its acquisition by Verizon, leading to a reduction in the purchase price by 350 million USD.
Response
An analysis of the breached data revealed an alarming number of accounts were protected by simple passwords like “123456” or “password”. Yahoo and the broader tech industry were pushed towards adopting more robust security measures, including enhanced encryption for passwords and the adoption of more secure multi-factor authentication (MFA) processes.
3. MySpace (2013)
In June 2013, MySpace experienced a major data breach that affected approximately 360 million accounts. The breach exposed a huge amount of personal data, including usernames, passwords, and email addresses. The data stolen was from the platform's older version, before a significant site redesign that occurred later that month. The cybercriminal behind this attack, known by the alias “Peace,” is the same person linked to other high-profile breaches.
Response
The MySpace breach occurred when awareness of digital privacy and security was heightening but still not at the forefront of social media users’ minds. The scale of the breach made it one of the most significant of its time—spotlighting the vulnerabilities of stored user data, especially passwords.
In response to the breach, MySpace invalidated all passwords for accounts created before the 2013 redesign, emphasizing the need for strong, regularly updated passwords. The breach underscored the importance of sturdy security measures and led to increased adoption of better practices across the industry, such as hashed and salted passwords, which are more resistant to hacking.
4. Adult Friend Finder Network (2016)
In 2016, the Adult Friend Finder Network suffered a massive data breach that exposed over 412 million accounts. The breach involved multiple sites within the network, including AdultFriendFinder.com, and resulted from a local file inclusion vulnerability. The exposed data included usernames, emails, login dates, and passwords, many of which were stored in plaintext or hashed using the weak SHA-1 algorithm, making them easy to crack. This breach was significant not only because of the volume of data exposed but also because it included details from accounts that had been deleted by users but were still retained by the company.
Response
After the breach, the Friend Finder Network took immediate steps to secure its systems, including patching the vulnerability and implementing site-wide password resets. The incident underscored the necessity for stronger security measures, such as the use of solid hashing algorithms and regular updating and auditing of security practices. It also highlighted the importance of ethical data retention practices, particularly concerning deleted accounts.
5. VKontakte (2016)
In June 2016, VKontakte (VK.com), a popular Russian social networking platform, experienced a significant data breach. A hacker acquired account details of over 100 million users, which included names, email addresses, and plaintext passwords. This data was then offered for sale on the dark web. The breach highlighted the platform's inadequate security measures, as the passwords were stored without encryption. The exposure of plaintext passwords posed a severe risk, potentially allowing attackers easy access to users’ accounts not only on VK but also on other platforms where users might have reused passwords.
Response
The breach served as a sobering reminder of the importance of strong password management and security measures. It prompted VK and other companies to reassess and strengthen their cybersecurity strategies, particularly focusing on the encryption of passwords and using more sophisticated authentication methods to better protect user data.
6. Aadhaar (2018)
In 2018, the Aadhaar database, which contains the biometric and personal information of over 1.1 billion Indian citizens, experienced a major data breach. This breach exposed sensitive information such as names, addresses, and other demographic details. The breach had significant implications for data security in India, raising concerns about the protection of personal information in large government databases.
Response
In response to the breach, there was increased scrutiny and calls for stronger data protection laws in India. The incident spurred discussions about implementing more robust security practices, including adopting better password management and authentication technologies to safeguard sensitive information. The breach also highlighted the need for continuous improvements in security infrastructure, and regulatory frameworks to protect personal data from unauthorized access.
7. Marriott International (2018)
The Marriott International data breach in 2018 was big news, affecting approximately 500 million guests. The breach originated in the systems of the Starwood Hotels group, which Marriott had acquired in 2016. The attackers had unauthorized access to the Starwood guest reservation database since 2014, but the breach wasn’t detected until September 2018 after Marriott received alerts from an internal security tool. The compromised information included names, mailing addresses, phone numbers, email addresses, passport numbers, Starwood Preferred Guest account information, date of birth, gender, and arrival and departure information. For many guests, encrypted payment card data was also compromised, with encryption keys being stolen.
Response
In response to the breach, Marriott not only addressed the immediate data exposure but also reviewed and strengthened their password and authentication systems to prevent these types of incidents in the future. However, Marriott also faced legal and regulatory repercussions, including a substantial fine under the GDPR in the UK due to the involvement of EU citizens’ data.
8. LinkedIn (2012 and 2021)
LinkedIn suffered two significant data security incidents, one in 2012 and another in 2021. In 2012, hackers compromised LinkedIn's network, leading to the exposure of 167 million user accounts, which included usernames, email addresses, and hashed passwords. This breach became public knowledge in 2016 when stolen data surfaced on the dark web. The 2021 incident involved the exposure of data scraped from around 700 million user profiles, which was then sold online. This dataset included email addresses, full names, phone numbers, physical addresses, geolocation records, and other professional details.
Response
The 2012 breach had a direct impact on password security as it demonstrated that hashed passwords that aren’t salted allow hackers to easily unscramble the passwords. This prompted LinkedIn to improve its hashing algorithms and introduce two-factor authentication (2FA) to bolster account security. The 2021 incident led to further scrutiny and calls for better protection against unauthorized data scraping, including reevaluating how user data is accessed and used by third-party apps and services.
9. Facebook (2019)
In 2019, a significant data breach exposed the personal details of approximately 540 million Facebook users stored on Amazon's cloud computing service. This incident involved two third-party Facebook app developers, Cultura Colectiva, and an app called “At the Pool.” The exposed data included account names, IDs, comments, reactions, and unprotected passwords for about 22,000 users from the “At the Pool” app. The breach primarily stemmed from improperly secured databases that were publicly accessible without proper protections.
Response
Following the breach, there was a notable push within the tech community for stricter controls and monitoring of third-party developers to prevent similar incidents. Facebook increased its scrutiny and auditing of apps on its platform, attempting to tighten access to user data. The breach also accelerated discussions around the necessity of strong password management and the implementation of MFA to enhance security. These measures are aimed at minimizing the risk of unauthorized access, even when user data is inadvertently exposed by third-party partners.
Read more: How to recover a hacked Facebook account
10. Alibaba (2019)
In 2019, one of the largest data breaches in history occurred involving Alibaba Cloud, where data from a Shanghai police database containing information on one billion Chinese citizens was left unsecured and publicly accessible for more than a year. This massive trove of 23TB of data included sensitive personal information such as names, birthdates, addresses, and national identification numbers. The breach was exposed when an anonymous user advertised selling this data for 10 bitcoin on a hacker forum.
The exposure of such a huge amount of sensitive data not only placed individuals' privacy at risk but also highlighted significant vulnerabilities in data security practices at Alibaba Cloud. This incident brought immense scrutiny from the Chinese government and the public, emphasizing the critical need for stringent security measures, especially when handling sensitive information on such a large scale. The breach had potential repercussions for the privacy of over 70% of the Chinese population, considering the scale of data involved.
Response
In light of the breach, Alibaba Cloud was compelled to reassess and fortify its password and authentication systems, among many other things. The incident also influenced stronger industry-wide practices around password security, urging other cloud platforms to strengthen their safeguards against similar vulnerabilities.
The evolution of digital passwords
While data breaches have undeniably served as a catalyst for reshaping password management practices, the evolution of these policies isn't solely driven by reactionary measures to cyber incidents. Technological advancements and ongoing research also play important roles, pushing the boundaries of what's possible in cybersecurity. Institutions like the National Institute of Standards and Technology (NIST) sit at the forefront of this movement, continuously adapting guidelines to stay one step ahead of emerging threats.
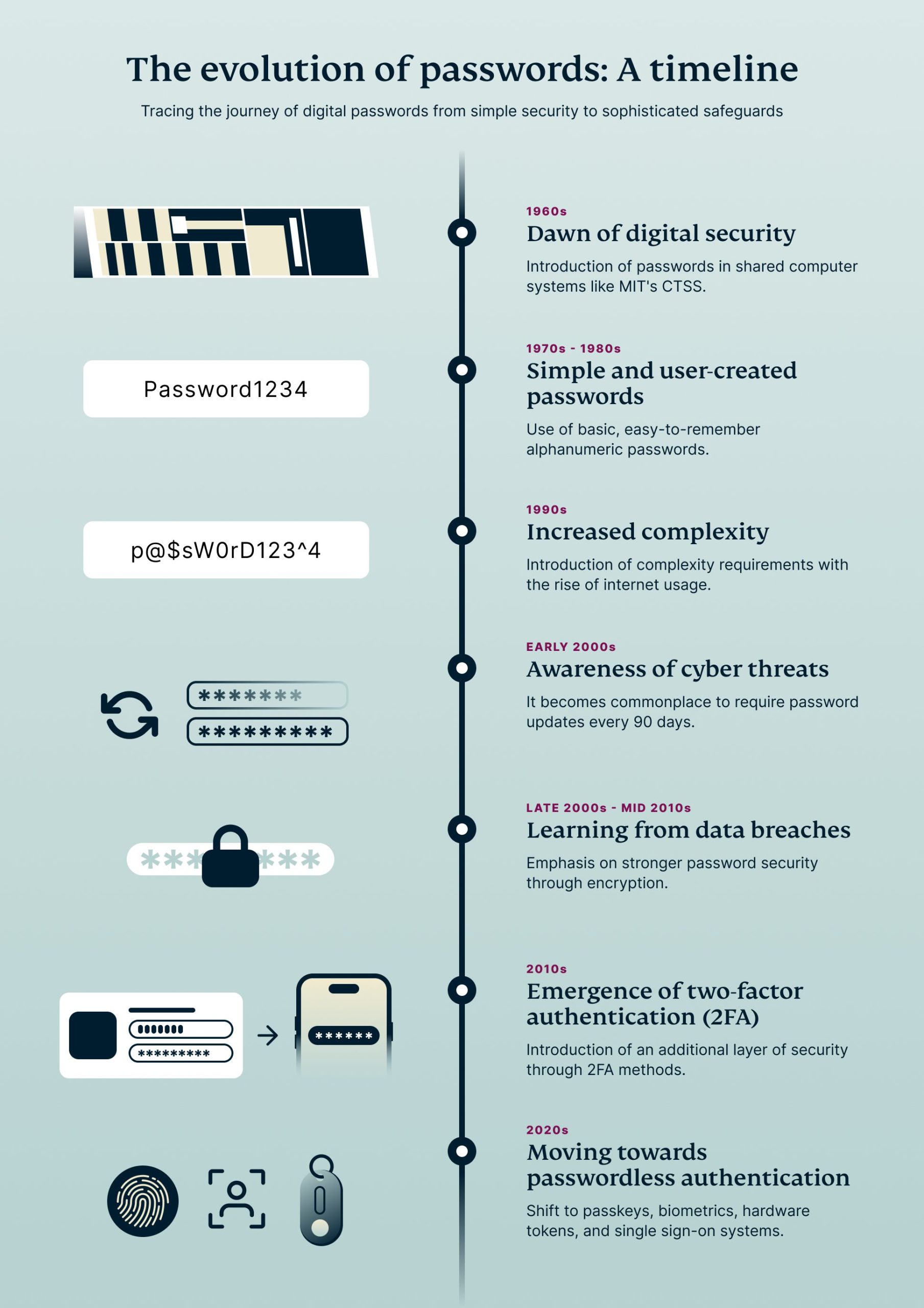
Back in the early days of digital authentication, crafting a password was simple—a straightforward word or a basic string of numbers often did the trick. But as the internet took off, so did cyber threats, necessitating a seismic shift in how we think about securing our digital doors. Initially, institutions like NIST championed complex passwords packed with a mix of numbers, symbols, and both uppercase and lowercase letters. This complexity was meant to thwart brute-force attacks, where attackers try every possible combination, and dictionary attacks, which deploy common words and phrases to breach accounts.
However, the focus solely on complexity began to shift as research showed that length and unpredictability could offer better security. NIST's 2017 guidelines marked a significant transformation in password security philosophy, advocating for longer passphrases that are easier for users to remember yet hard for attackers to guess. These guidelines moved away from mandatory complex character combinations, highlighting instead the importance of password length and the avoidance of predictable patterns.
The risk of password breaches, whether through social engineering or the use of weak passwords, has driven changes in authentication practices. No longer is a lone password for authentication considered secure. Multi-factor authentication, often in the form of one-time passwords, biometrics, authenticator app, or hardware key, are now seen as indispensable, especially in a work setting.
Best practices for password management
Nowadays, managing a slew of passwords has become a common headache for many of us. This often leads to “password fatigue,” where the effort to remember several complex passwords results in unsafe practices like reusing the same password across multiple sites. This scenario is far from ideal as it presents a significant security risk—one compromised password can potentially give attackers access to numerous accounts.
Read more: How much time do you waste resetting your passwords?
To combat these issues, there’s been significant progress in password management technology. Password managers now play a role in helping to keep track of our passwords by storing them in encrypted formats. One primary password gets you access to all your passwords. Not only do you no longer have to remember every password but this system also enables you to create complex, long, nonsensical passwords that would take hundreds of years to crack.
Furthermore, technologies like 2FA and MFA are becoming standard, adding an extra layer of security that goes beyond the traditional password. There are also proactive steps that individuals and organizations can take right now to safeguard their digital lives:
| Individuals | Organizations |
| Use strong passwords: Opt for long, complex passwords that are randomly generated, and make each one unique. This enhances security significantly. For an additional layer of protection, enable two-factor authentication (2FA), making your accounts harder to breach even if a password is compromised. | Use Single Sign-On (SSO) Technology: SSO can reduce password fatigue and security risks by allowing employees to access multiple applications with one set of credentials, managed and secured centrally. |
| Opt for password management: Better yet, use a password manager like ExpressVPN Keys, which is included with every ExpressVPN subscription. One primary password gives you access to all your passwords. Not having to remember them, you can make your passwords as long and random as you’d like. | Embrace MFA: Beyond just passwords, organizations should implement additional layers of security. MFA requires users to verify their identity using something they know (a password), something they have (a security token), or something they are (biometric verification), adding an extra barrier against unauthorized access. |
| Enable account notifications: Stay informed of any unusual activity by enabling notifications for account logins and changes. This way, if someone tries to access your account or changes your security settings, you'll receive an alert immediately and can take appropriate action. | Educate your workforce: Conduct advanced cybersecurity training that goes beyond basic password management to include real-world simulations of phishing and other cyber threats. This helps employees recognize and respond to security threats effectively. |
The future of passwordless authentication
While society has made major improvements in managing passwords, the traditional password system is on its way out because it simply can’t keep up with today’s security threats. Passwords are a hassle to manage, easy to forget, and all too often, they’re the weak link that hackers exploit. That's why big tech companies like Apple, Google, and Microsoft are pushing for a shift to something better: passkeys.
Passkeys cut out the need for the passwords we struggle to remember and instead use a pair of cryptographic keys. The public key lives on the server and the private key stays with you, locked in your device, often secured further with something like your fingerprint, face ID, or a PIN.
Passwordless authentication is not susceptible to the main risks associated with setting passwords. For someone to log in as you, they would need to have your physical device. Even then, without your biometrics (or PIN) they wouldn’t be able to gain access. And using passkeys means data breaches won’t compromise your login: If someone hacks into a company server, for instance, they wouldn’t be able to discover your password—because it doesn’t exist.
However, while passkeys offer significant advantages, widespread adoption hasn't kicked off yet. Many users and organizations need time to understand how they work and integrate them into their systems, which involves both financial and logistical considerations. Plus, many still prefer the familiarity of traditional passwords, despite their shortcomings.
For now, while we're in this transition phase, keeping your current passwords randomly generated and secure is key. The simplest way to do that? You guessed it: with a password manager.
FAQ: About the evolution of passwords
What is the largest data breach in history?
What’s a good password manager?
ExpressVPN Keys is a good option for a password manager, especially if you are an ExpressVPN subscriber, as it comes included with every subscription. It operates on a zero-knowledge security model, which ensures that only the user has access to their passwords. It supports synchronization across multiple devices, making it easy to manage passwords securely wherever you are.
In addition to Keys, other reputable password managers include LastPass, 1Password, and Dashlane. These platforms are known for their strong security features, such as encrypted storage and multi-factor authentication. They also offer user-friendly interfaces, secure password-sharing options, and the ability to generate strong, unique passwords for each site, enhancing your overall online security.
How do I find my passwords on my iPhone?
- Open settings: Tap the Settings icon on your iPhone's home screen.
- Access passwords: Scroll down and tap on "Passwords".
- Authenticate: You will be prompted to authenticate using Face ID, Touch ID, or your device passcode.
- View passwords: Once authenticated, you'll see a list of websites and apps for which you've saved passwords. Tap on any entry to view the password details.
How do I find my Google password?
- Go to Google's Account Recovery page:
- Visit the Google Account Recovery page by typing "Google account recovery" in your web browser or navigating directly to https://accounts.google.com/signin/recovery.
- Enter your email: Type the email address you use for your Google account and proceed by clicking on 'Next'.
- Follow the prompts: Google will guide you through steps to verify your identity. This might include answering security questions, verifying a code sent to your phone, or confirming a message on a linked device.
- Reset password: Once your identity is confirmed, you will be given the option to create a new password. Choose a strong, unique password to help secure your account.
Remember, if you’ve saved your Google password in a web browser or password manager, you can also retrieve it from there by looking in the respective passwords section of the settings menu.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN