Brute force attack: What it is and how to prevent it
A brute force attack is exactly what it sounds like: instead of looking for a secret way into your accounts, attackers just try thousands of different combinations until they find one that works. They use specialized software that can fire off thousands of guesses in seconds. It’s not smart or subtle; it’s just relentless.
These attacks primarily go after passwords, but they can also target other sensitive data like encryption keys and Secure Shell (SSH) credentials. And the bad news is that if your defenses are weak, a brute force attack has a good chance of working. All it takes is one weak or reused credential.
We’ll walk you through how brute force attacks work, the tools behind them, and how to protect your accounts and data.
What is a brute force attack?
A brute force attack is when attackers try to access an account or system by guessing passwords, encryption keys, or other sensitive data. They use automated tools to test thousands of guesses per second. It’s not sophisticated; it’s just trial and error, done fast and at scale.
Brute force attacks can hit anything with a login, including email, cloud storage, social media, admin panels, and even Wi-Fi. If there’s no protection against repeated attempts, it’s vulnerable.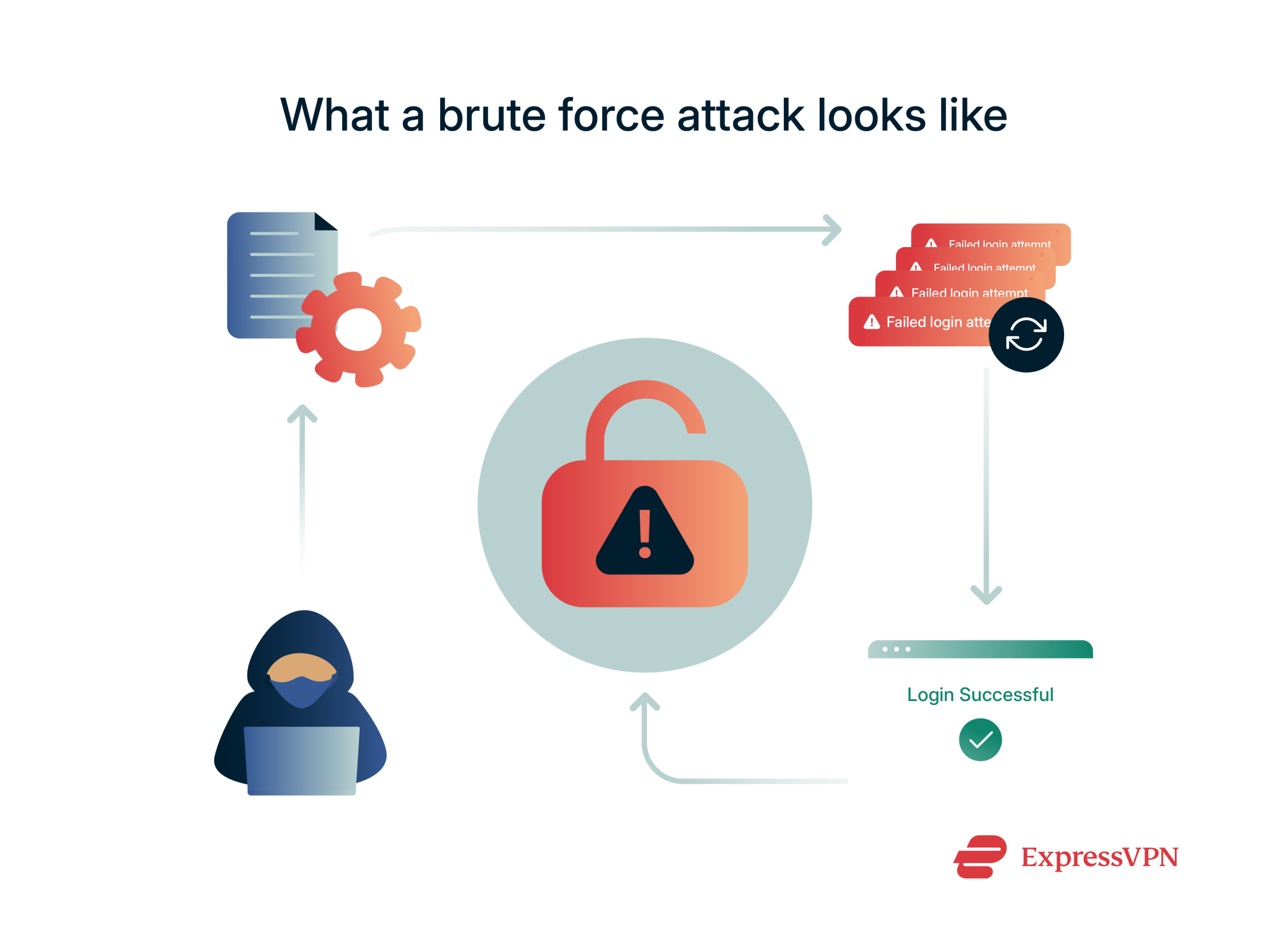 These attacks are more likely to succeed when systems have:
These attacks are more likely to succeed when systems have:
- Short or common passwords.
- Reused credentials.
- No login attempt limits.
- No two-factor authentication (2FA).
And these habits are surprisingly common. Most people rely on just three passwords across all their accounts, and around one in eight people use the same password for everything. That gives attackers a huge advantage.
Even without advanced tools, guessing the right combination becomes a lot easier when people fall into predictable patterns.
How does a brute force attack work?
A brute force attack works by trial and error. Automated tools run through huge numbers of password guesses, often starting with the most common ones: simple phrases, reused logins, or patterns like “summer123.”
For example, if the password is “summer2024,” a tool might try “summer,” “summer1,” “summer123,” and so on, until it hits the right one.
Tools like Hashcat or Hydra run non-stop, testing millions of passwords quickly, often using leaked data or common patterns. When paired with powerful hardware or run across botnets, they can try even more guesses in less time.
Some attacks focus on a specific account. Others target many accounts using a list of usernames and testing known passwords. If there’s no rate limiting or 2FA, this method can work.
For real-world examples of how these attacks are used, check out this guide to brute force hacks.
Why are brute force attacks dangerous?
Brute force attacks don’t need much to work, just a login form, time, and a weak or reused password. If a credential has been exposed in a breach, it can be cracked in seconds.
The real danger is scale. Attackers can hit thousands of accounts at once using automated tools and giant lists of known passwords. Any successful attempt can lead to stolen data, unauthorized access, or, in some cases, full account takeovers or ransomware attacks.
These attacks are still common because weak passwords and missing 2FA are also unfortunately common, and fast password-cracking tools are easy to come by.
Types of brute force attacks
All brute force attacks aim to guess the right password or key, but the methods vary. It depends on how much information the attacker has and what kind of system they’re targeting.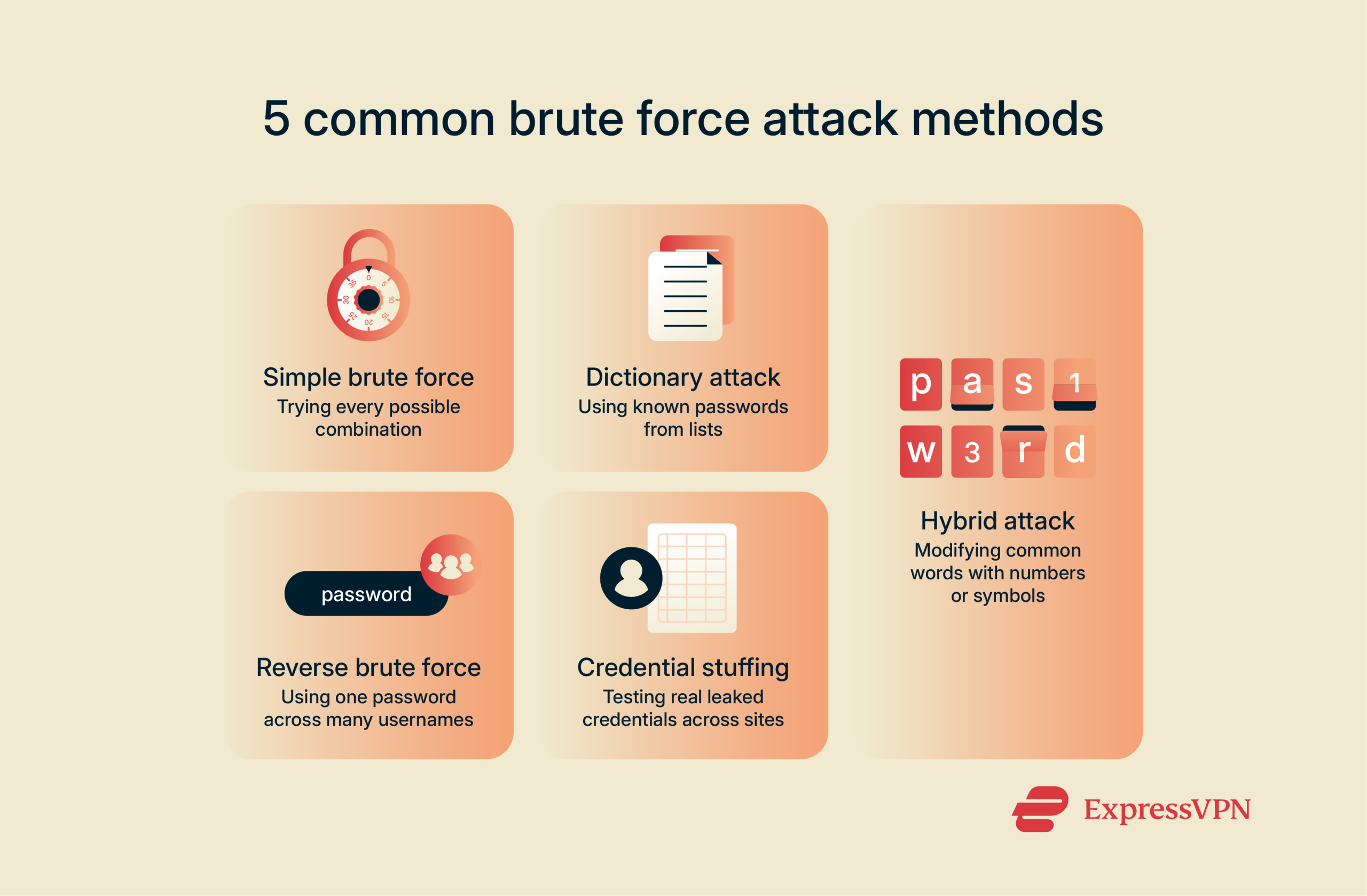
Simple brute force attack
This is the most straightforward type. The attacker goes through every possible password combination, one by one, until something works.
There’s no guesswork or shortcuts; it’s a full sweep. A short password like “1234” might take seconds. A long, complex one could take many years. The only limit is how fast the attacker can try each guess and whether the system puts any blocks in the way.
Because it tests everything, this method takes time, but it will eventually work unless something stops it, like long, complex passwords, 2FA, or login attempt limits.
Dictionary attack
A dictionary attack uses a list of likely passwords instead of trying every possible combination. These lists are built from real-world data, like leaked passwords, common patterns, and actual dictionary words.
If your password is something familiar like “sunshine” or “qwerty123,” it’s probably in there. This method works because most people use predictable passwords; if yours is based on a single, common word, especially without modifications, it’s at risk.
Hybrid brute force attack
Hybrid attacks combine two strategies: start with a common word or phrase, then add the kinds of tweaks people typically use to turn it into a password.
In other words, most people don’t use truly random strings. They take a word they remember, like “sunset,” and add a number, a year, or a symbol to make it “secure.” So instead of guessing every possible password, hybrid attacks focus on those realistic patterns: “Sunset1,” “sunset2023,” “$unset,” and other familiar variations.
It’s faster than brute force, smarter than a simple dictionary attack, and surprisingly effective because it’s built around how people actually think. The more predictable the pattern, the easier it is to break.
Reverse brute force attack
Many brute force attacks start with a username and try to guess the password. Reverse brute force attacks work the other way around. Instead of picking one user and trying lots of passwords, the attacker takes one common password, like “123456,” and tries it across a huge list of usernames.
They’re betting that someone, somewhere, is still using that password. And if just one account matches, that’s all they need.
Credential stuffing attack
Credential stuffing uses real usernames and passwords, usually leaked in data breaches, and tries them on other sites and services.
Since people reuse passwords, attackers run those combos through tools to test logins on email, banking sites, and more. They’re not guessing; they’re testing what’s already known. That’s what makes it so effective, and that’s why it’s so important to use a unique password for every account.
If an attacker gets into your Google or Facebook account, you may want to delete your search history or even permanently delete your Facebook account to protect your data.
How hackers execute brute force attacks
Brute force attacks are almost always automated. Hackers use tools that do the work for them, trying thousands of password combinations, over and over, until something works.
These attacks don’t take much skill. With basic tools and a decent internet connection, anyone can run one.
Automated tools used for brute force attacks
Some tools, like Hydra, go after websites directly, testing logins in real time. Others work offline, testing stolen password data. In offline attacks, tools like Hashcat or John the Ripper try different guesses against the hashes (the encrypted versions of passwords stored by websites) without ever touching the live system.
Either way, they guess thousands of passwords in seconds using automation. Attackers often load in leaked credentials or common passwords, and the tool automatically generates variations, like adding numbers or symbols, before running through them at speed.
How GPUs accelerate brute force attacks
Brute force attacks are all about speed. The faster a system can try passwords, the more likely it is to find the right one. That’s where GPUs come in.
They’re usually used for things like gaming or video editing, but they’re also great at doing lots of repetitive tasks quickly. Password guessing is exactly that. When a data leak has exposed a hashed password, hardware acceleration can be used to pass millions of passwords per second through the hashing function to find a match for the original password
That kind of speed makes brute force attacks faster and more dangerous than ever.
Impact of internet speed and server power
When brute force attacks hit live systems, like websites or login pages, speed changes everything. A fast internet connection lets attackers send more guesses faster. Some spread the load across multiple devices or botnets to push even harder.
What really matters is how the server handles it. If it doesn’t slow things down or block repeated attempts, the attack keeps going. That’s why protections like rate limits and account lockouts, which temporarily block access after too many failed attempts, make a difference. They don’t stop attacks completely, but they do throw up roadblocks.
Most common brute force attack tools
Brute force attacks depend on the right tools, which are fast, flexible, and often free. Some crack stolen password data. Others target live login forms. Most can be customized for different attack styles, from guessing weak passwords to testing leaked credentials.
Please note: We’re sharing these examples purely for educational and awareness purposes. Our goal is to help you recognize potential threats, not to promote or encourage their use.
| Tool | Primary use | Mode of operation | Key features |
| John the Ripper | Cracking password hashes | Offline | Fast, lightweight, supports multiple formats and GPU acceleration |
| Hashcat | Cracking password hashes | Offline | GPU-accelerated, flexible attack modes |
| Hydra | Cracking login credentials | Online | Supports many protocols, automated testing |
| Aircrack-ng | Breaking Wi-Fi passwords | Offline/Online | Specialized for wireless networks |
| Nmap (NSE) | Testing weak credentials | Offline | Integrated with network scanning |
John the Ripper
John the Ripper is a classic password-cracking tool, known for being fast, flexible, and easy to use. It’s mostly used for offline attacks where attackers already have stolen password hashes and want to crack them.
It supports dictionary attacks, brute force, and hybrid methods, and it works with many password formats. What makes it popular is how lightweight it is. It runs fast, doesn’t need fancy hardware, and works well even on older machines.
For attackers trying to break into hashed passwords, which are encrypted versions of passwords stored by websites, John is often the go-to starting point.
Hashcat
Hashcat is also a tool used to crack passwords offline. It’s known for using GPU power to speed up the process, testing huge numbers of guesses per second.
It supports different attack methods and can be configured to try specific patterns, password formats, or rules. That flexibility makes it useful for attacks that need to cover a lot of ground quickly.
Hydra
Hydra is a tool used to crack usernames and passwords for remote services accessed over the internet, like SSH (used to remotely access systems), File Transfer Protocol (FTP, for transferring files), websites, and remote desktops.
Instead of guessing one password at a time, Hydra can run through lists of usernames and passwords automatically. It checks combinations across different services until one works or until it gets blocked.
It’s often used to find weak login points on systems that don’t limit attempts or use extra layers of security.
Aircrack-ng
Aircrack-ng is used to break into Wi-Fi networks. It works by deauthenticating a device, which prompts the device to restart its connection to the router, making it possible to capture the four-way handshake between the client and the router.
At that point, Aircrack-ng can perform an offline attack on the captured handshake to recover the correct WiFi password. If the network uses a weak password, this doesn’t take long. Aircrack-ng is often used to test how secure a Wi-Fi setup really is, but in the wrong hands, it can be used to get into networks that aren’t properly protected.
Nmap brute-force modules
Nmap is mainly used to scan networks, but it also includes scripts that can run brute force login attempts. These Nmap Scripting Engine (NSE) modules can test common usernames and passwords against services like SSH, FTP, and web logins.
It’s not the fastest option, but it’s useful if someone is already scanning a system and wants to check for weak credentials along the way. It’s often part of routine security testing.
How to protect your passwords from brute force attacks
Brute force attacks depend on weak or reused passwords. That’s why the best defense is making your passwords harder to guess and not reusing the same password across accounts. A few small changes make a big difference.
Using long and complex passwords
Long, random passwords are harder to crack. Every extra character makes brute force attacks slower and less likely to work.
Use a password manager and a secure password generator to create and store strong passwords so you don’t have to remember them all. ExpressVPN Keys is a great choice for easily managing strong, unique passwords across your devices.
Enabling two-factor authentication (2FA)
2FA adds a second step to your login, like a code sent to your phone or an app. Even if someone guesses your password, they can’t get in without that second code. It’s one of the simplest and most effective ways to stop brute force attacks cold.
How hashing and salting protect passwords
Websites don’t store your actual password; they store a scrambled version called a hash. Hashing turns your password into a string of characters that can’t be reversed.
Salting adds random data to that password before hashing it, making each hash unique, even if two people use the same password. This makes brute force and dictionary attacks much harder.
Implementing rate limiting to block multiple attempts
Rate limiting slows down how often someone can try to log in. After a few failed attempts, the system blocks or delays more tries. This makes brute force attacks take longer and often means the attacker won’t bother trying.
Using CAPTCHA as an additional security layer
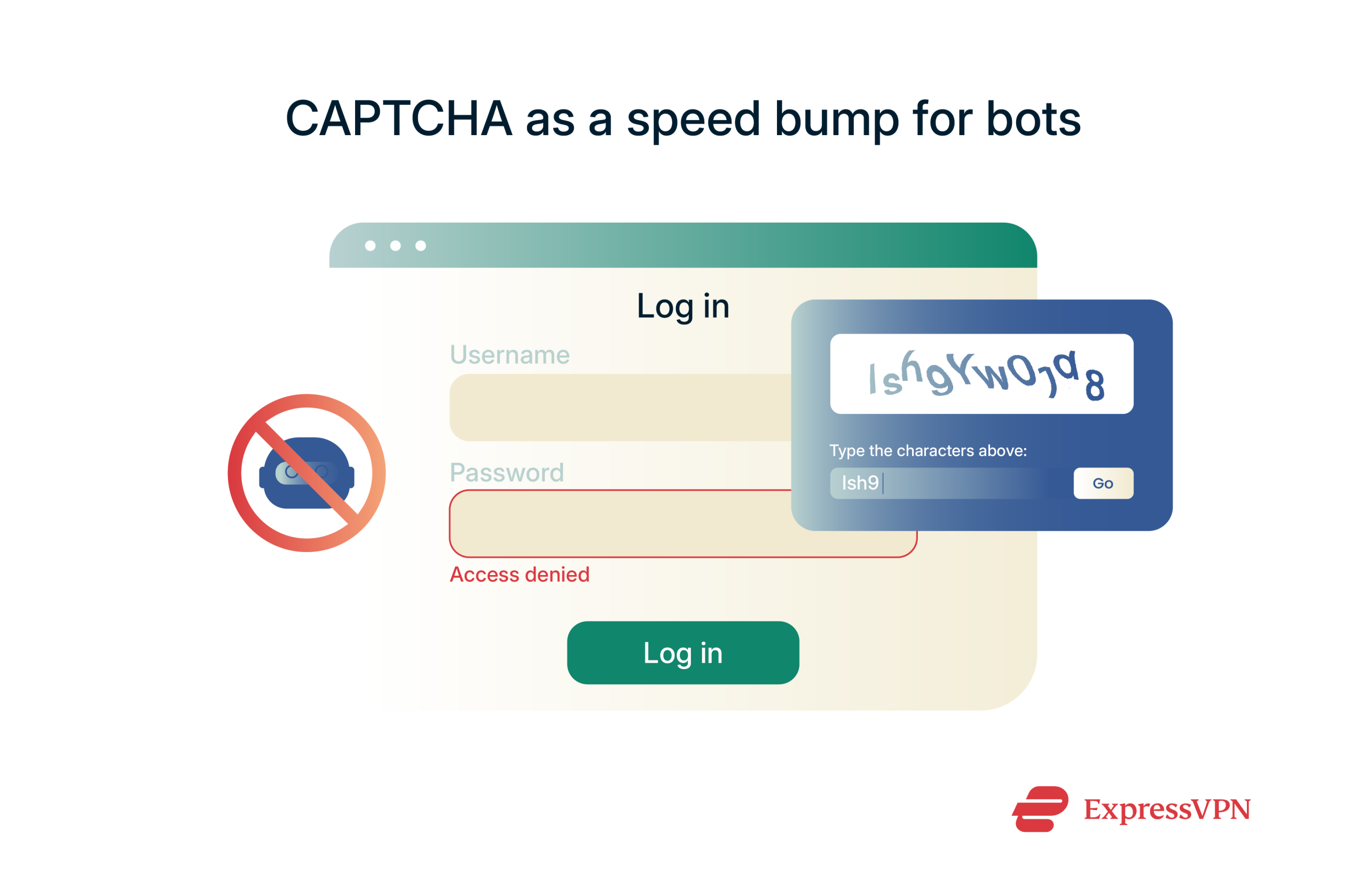 CAPTCHAs stop bots by making users prove they’re human, usually with a quick test like identifying images or typing distorted text.
CAPTCHAs stop bots by making users prove they’re human, usually with a quick test like identifying images or typing distorted text.
They don’t block all brute force attacks, but they slow down many automated tools, especially more basic ones. However, some advanced bots can bypass CAPTCHAs using image recognition or third-party solving services. Nonetheless, adding this extra step still helps reduce mass login attempts.
How long does a brute force attack take?
It depends on three things: the strength of the password, the power of the attacker’s hardware, and how much info they already have. When it comes to offline attacks, the strength of the hashing algorithm used by the relevant website is also a factor.
A simple password like “qwerty123” might crack in seconds. A random 16-character password? That could take billions of years to crack with current technology.
Let’s break it down further.
Longer passwords = More time to crack
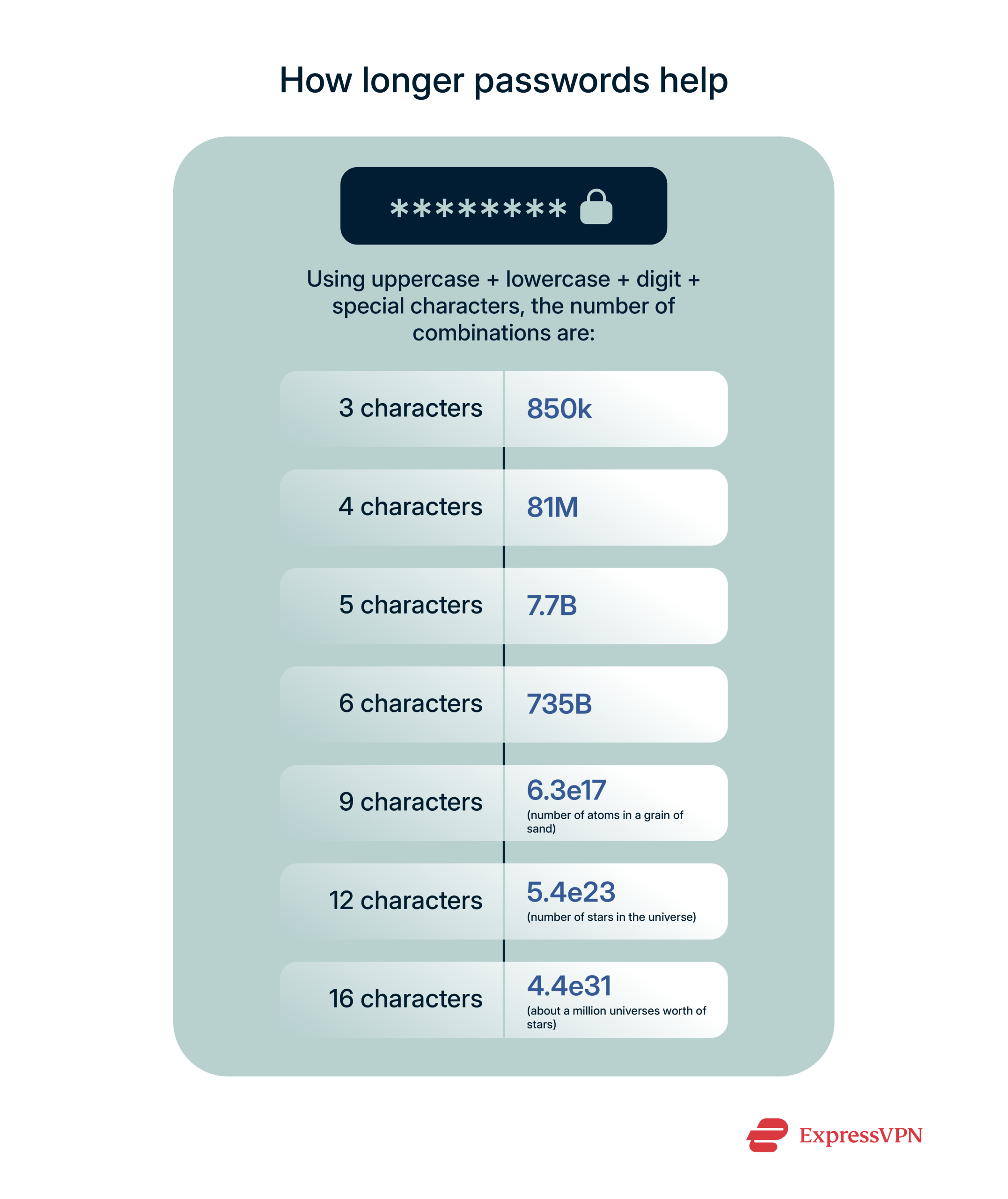 Every character you add makes a password harder to break. A short password might have millions of possible combinations. A long one? Trillions.
Every character you add makes a password harder to break. A short password might have millions of possible combinations. A long one? Trillions.
That extra length slows brute force attacks way down and sometimes makes them impossible.
Faster hardware = Shorter cracking time
Powerful hardware means more guesses per second. A setup with multiple GPUs can test millions, or even billions, of passwords quickly.
What used to take days can now take minutes, depending on the password’s strength.
More available information = Faster brute force attack
If an attacker already has part of your login, like your email or a leaked password, they don’t have to start from scratch.
The more they know, the fewer guesses they need. That makes brute force attacks faster and more likely to succeed.
Brute force attacks and encryption: What you need to know
Encryption is meant to protect data, even if it falls into the wrong hands. But not all encryption is equal, and brute force attacks can still be a threat if the encryption is weak or outdated.
What is an encryption key?
An encryption key is a string of data used to lock (encrypt) or unlock (decrypt) information, like a password, but for your files or messages. When something is encrypted, it turns into unreadable text unless you have the right key to decrypt it.
The key itself is just a random string of bits, but its strength lies in its complexity. The longer and more complex the key, the harder it is to guess using brute force. Some modern encryption keys are so strong that, even with today’s computing power, they’d take billions of years to crack.
Difference between 128-bit and 256-bit encryption
Both 128-bit and 256-bit encryption are considered secure, and so far, neither has been cracked. It would take a quantum computer billions of years to crack 128-bit encryption, but 256-bit is twice as long as 128-bit, meaning the number of possible combinations is squared.
A computer checking millions of combinations per second would still need over a sexdecillion years (that’s a 1 followed by 51 zeroes) to brute force a 256-bit key (that’s a year for every atom in the sun). That’s why most secure services use 256-bit encryption to protect your data.
How encryption helps prevent brute force attacks
Strong encryption makes brute force attacks nearly impossible. Even if attackers get their hands on the data, they can’t read it without the key, and cracking that key would take more time and power than today’s computers could ever deliver.
That’s why ExpressVPN uses 256-bit Advanced Encryption Standard (AES) encryption to protect everything you do online. Even if your traffic is intercepted, the encryption makes it unreadable; no one can brute-force their way in.
Just keep in mind: VPN encryption protects your data in transit, but it doesn’t replace strong passwords or 2FA. Use a VPN as part of your security toolkit to add a powerful layer of privacy that keeps your information out of the wrong hands. The better the encryption, the safer your data.
FAQ: Common questions about brute force attacks
Are brute force attacks illegal?
How common are brute force attacks?
How can I tell if my account was targeted by a brute-force attack?
If you see any of these signs, it's important to change your password immediately, enable two-factor authentication, and review your account for any unauthorized activity or changes.
How long does it take to crack an 8-character password?
What are the best practices to protect against brute force attacks?
Can brute force attacks be detected in real time?
What’s the difference between brute force and dictionary attacks?
Which websites are most vulnerable to brute force attacks?
Do brute force attacks still work?
How do companies detect and prevent brute force attacks?
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN

















Comments
Oky...
I need to reference your for an assignment, what is your last name?
I'm very flattered! My name is Lexie M. Having only one letter in my last name can be quite an inconvenience...
fDrt(xg8pgYl{wN~n