How to trace an IP address—Step-by-step guide


Ever wondered exactly how to trace an IP address—and what information it can reveal about you or someone else online? Whether you're investigating suspicious activity, protecting yourself from cyber threats, or curious about your digital footprint, knowing how to track an IP is a valuable skill to have.
This comprehensive guide covers everything you need: from simple tracing methods to advanced IP-tracking techniques used by cybersecurity professionals. You'll learn exactly how IP tracing works, when it’s legal and ethical, the risks involved, and, most importantly, how to protect your IP address from unwanted tracking.
What is an IP address and how does it work?
An IP address, or Internet Protocol address, is a unique string of numbers—or numbers and characters—every device needs to connect to the internet. It acts like a digital identifier, telling devices, websites, and services where to send and receive data. Without an IP address, browsing the web, streaming videos, or even sending an email wouldn’t be possible.
While your IP address doesn’t pinpoint your exact home address, it can be used by websites and apps to deliver location-based content or monitor traffic. This makes knowing how to trace an IP address valuable for legitimate purposes like investigating suspicious activity, but it also highlights important privacy considerations.
Your Internet Service Provider (ISP) assigns you an IP address when you go online. If you’re at home, your Wi-Fi router has a public IP that covers all connected devices. When using mobile data, your phone gets an IP address from your carrier, while public Wi-Fi networks assign a shared IP to everyone connected.
These IP addresses typically change depending on the network. However, some online activities, such as gaming, web hosting, or remote access, often require consistency in your IP. That’s why knowing how to configure a static IP address can be especially useful.
IPv4 vs. IPv6—What’s the difference?
IP addresses come in two versions: IPv4 and IPv6. Internet Protocol version 4 (IPv4) is the older and most commonly used version. It consists of four sets of numbers separated by dots—for example, 192.168.1.1. Initially, IPv4 provided around 4.3 billion unique IPs. However, the explosion of devices connected to the internet means we've reached "IP address exhaustion," where we're rapidly running out of available IPv4 addresses.
Internet Protocol version 6 (IPv6) was introduced to fix this problem. It uses a much longer and complex format with a mix of numbers and letters, like 2001:0db8:85a3::8a2e:0370:7334. This expanded structure provides a colossal number of unique addresses, ensuring the internet can continue growing. IPv6 is also designed to be more efficient and secure than its predecessor.
Even though IPv6 adoption is increasing, many websites and networks still rely on IPv4. Since both versions remain in use, most modern devices and ISPs support them simultaneously, ensuring seamless connectivity no matter which protocol is in play.
Why would you want to trace an IP address?
Knowing how to trace an IP address can be incredibly useful for businesses, security professionals, and even everyday internet users. Though it won’t tell you exactly where someone is, it can give you clues about whether a connection is safe or potentially risky.
Cybersecurity and fraud prevention
Businesses and financial institutions regularly trace IP addresses to prevent fraud and unauthorized transactions. For example, online retailers often compare a customer’s IP address with their billing address. If a purchase suddenly originates from an IP address in a different country, it's a clear sign something isn't right—helping prevent fraudulent transactions.
Security teams also monitor IP addresses to defend against cyber threats like DDoS attacks, where hackers flood websites with traffic to take them offline. If security software detects repeated suspicious activities from specific IPs, teams can quickly block these addresses to stop potential attacks.
On a personal level, knowing how to track an IP address helps identify unauthorized access to your home network or accounts. If you notice unfamiliar IP addresses logging in to your Wi-Fi or personal accounts, someone may be trying to hijack your connection or steal sensitive information. Being able to quickly identify and respond to it can protect you from further harm.
Identifying suspicious or malicious activity
Every time you log in to an account, visit a website, or connect to a network, your IP address is logged. This helps security systems detect anything unusual—like an unexpected login from another country. If you’ve ever received a security alert about a login from a device or location you don’t recognize, that’s IP tracking at work.
Hackers frequently attempt to breach accounts by guessing passwords or testing stolen credentials. IP tracing helps identify these attempts early, allowing platforms to automatically block suspicious IP addresses and prevent unauthorized access.
Tracking a lost or stolen device
If your device gets lost or stolen, an IP address can sometimes provide clues about its whereabouts. If your device connects to the internet, it receives an IP from the network it's on. Tracing this IP address can give you a general idea of its location—whether it's nearby or has moved far away—helping you take appropriate action.
Locating the origin of an email or website
Email addresses and websites can easily be faked, but IP addresses are much harder to disguise. Take phishing emails, for example—they might claim to be from your bank, but checking the sender’s IP can tell a different story. If you find an IP address from an email actually traces back to a completely different country, that’s a clear red flag.
Similarly, IP tracking can confirm whether an online store is genuinely based where it claims to be. Fraudulent websites sometimes pretend to operate from reputable locations, only to disappear after stealing customers' money or personal data. Knowing how to trace an IP address helps you determine whether a site is trustworthy before sharing sensitive information or payment details.
Monitoring unauthorized network access
If your internet connection suddenly slows down or behaves strangely, checking the IP addresses of connected devices can help you spot unauthorized users. Unsecured Wi-Fi networks are an easy target for cybercriminals, neighbors looking for free internet, or even devices infected with malware that secretly communicate with external servers.
Most routers allow you to view a list of connected devices, each with its assigned IP address. If you notice unfamiliar IPs, it could mean someone is piggybacking on your network or worse—trying to access your data.
How to trace an IP address—best methods & tools
Tracing an IP address doesn’t require advanced technical skills—built-in tools for Windows, Mac, and Linux simplify the process. Whether you’re troubleshooting network issues, verifying connections, or investigating suspicious activity, here’s exactly how to trace an IP address quickly and easily.
Using command line tools (Windows, Mac, Linux)
Your operating system comes with built-in tools that help trace the route data takes across the internet. The process differs slightly depending on your operating system, but they’re all easy to carry out—just follow the instructions below to track an IP address in minutes.
Tracing an IP with the "tracert" command (Windows)
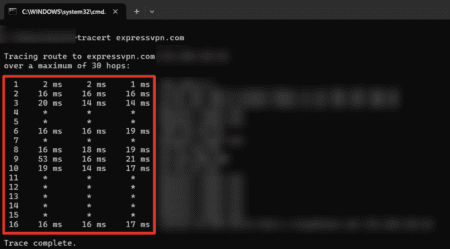
If you’re using Windows, the “tracert” command is your go-to tool for tracing an IP address. It works by sending packets to the target and listing each hop the data takes along the way. This helps you see the path your connection follows and identify where delays or issues might be occurring.
- Press the Windows key + R, then type in “cmd”, and press Enter.
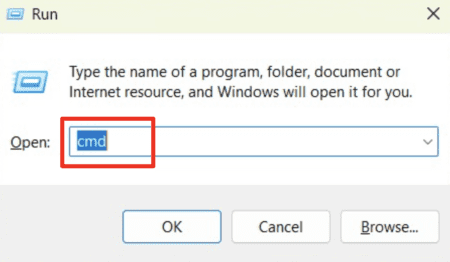
- Type in “tracert [IP address or website domain]” to run the tracert command. For example, your command could be “tracert expressvpn.com”.
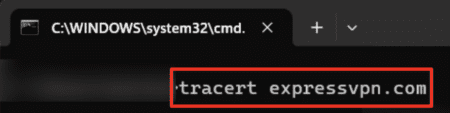
- Analyze the results. Each line represents a different hop, showing the IP address of the router it passed through and the response time for each attempt. If you see “* * *,” it means a hop didn’t respond due to a firewall or network restrictions.
Using "traceroute" on macOS and Linux
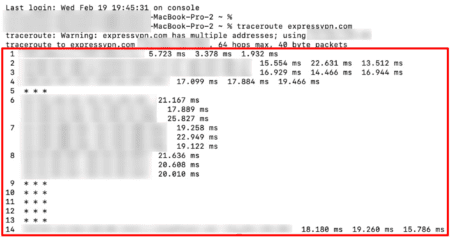
On Mac and Linux, the command is slightly different—it’s called traceroute instead of tracert, but it works the same way.
- Open the Terminal. On macOS, press Command + Space, type in “Terminal,” and hit Enter. On Linux, open the Terminal from your applications menu or use “Ctrl + Alt + T.”

- Type in “traceroute” followed by the IP address you’re looking for or a website domain, for example, “traceroute facebook.com”. Press Enter to run the command.

- The output shows all the servers or routers your connection travels through. The further down the list, the closer you are to the destination. If certain hops show “* * *,” it could indicate firewalls are blocking responses or restricted networks.
Finding an IP address from an email header
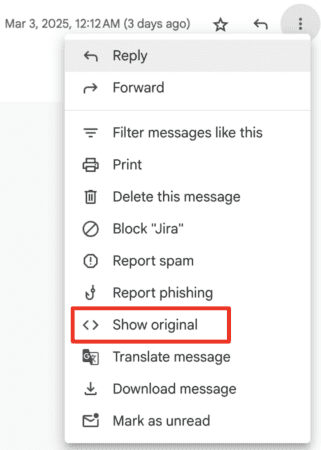
Emails contain hidden information called headers, which can show the sender's IP address. However, some services, like Gmail or Outlook, may mask IPs for privacy.
- Open the email, tap on the three dots icon, and select “View Source” or “Show Original” (this varies by provider).
- Look for the line that starts with “Received: from”. This will show the servers the email passed through.

- The sender’s IP is usually in the first "Received" line that includes an IP address in brackets [ ], such as: “Received: from mail.example.com (192.168.1.1)”.
- Copy the IP and run it through an IP lookup service to get more details on its location and network.
Using online IP lookup services
If you already have an IP address to trace, online lookup services can quickly provide location, ISP, and sometimes historical usage data. While they don’t offer pinpoint accuracy, they can help identify whether an IP belongs to a residential network, a data center, or even a known VPN or proxy service.
Popular free IP lookup services like WhatIsMyIP.com, IPinfo.io, and MXToolbox pull data from public records and geolocation databases to display the country, city, and ISP associated with an IP. Security-focused tools, such as AbuseIPDB and VirusTotal, go a step further by flagging IP addresses linked to spam, fraud, or other suspicious activity.
For a quick way to check your own IP address and the information it reveals, try ExpressVPN’s IP checker.
How to trace an IP address with WHOIS lookup
WHOIS lookups provide ownership information about IP addresses or domain names, revealing who manages a specific IP range or website. It’s perfect for verifying legitimacy or investigating suspicious networks.
- Visit a WHOIS lookup service, like whois.domaintools.com or whois.arin.net
- Enter the IP address or domain name you want to trace.
- Review the results to see the organization, ISP, and contact details if they’re publicly available. Personal user IPs are often masked for privacy.
Tracking IPs with network monitoring tools
Businesses, IT teams, and cybersecurity professionals frequently trace IP addresses in real-time with network monitoring tools. These advanced tools track connections, detect unauthorized access, and help maintain secure networks. Most widely used tools for tracking IPs and monitoring network activity include:
- Wireshark – Powerful packet analyzer for detailed network inspection.
- PRTG Network Monitor – Comprehensive tool to track IPs, network traffic, and uptime.
- SolarWinds IP Address Manager – Manages IP addresses, allocation, and conflicts.
- Angry IP Scanner – Quickly scans networks for active IP addresses.
Reverse IP lookup—What it can and can’t do
A reverse IP lookup lets you see which domains are linked to a specific IP address. This can help identify shared hosting environments, analyze websites, detect connections between domains, and uncover hidden or fraudulent sites.
- Choose a reverse IP address lookup service, like ViewDNS.info, SecurityTrails, or Spyse.
- Type the target IP address into the lookup tool’s search bar and run the query.
- The tool will return a list of domains currently hosted on that IP. If the IP belongs to a shared hosting provider, you may see multiple websites listed. If the IP is dedicated to a single entity, only one domain might appear.
A reverse IP lookup is useful, but it cannot:
- Identify the exact owner of a website or IP address for privacy reasons.
- Reveal personal user information.
- Track real-time website activity—it only provides static information about hosted domains.
While useful for website research, reverse IP lookup is not a tool for tracking individuals—it’s mainly used for security analysis and network diagnostics.
Can you get someone’s exact location from an IP address?
If you want to know how to trace an IP address, you also need to learn its limitations.
It can provide a general idea of someone’s location—typically, it's accurate to a city or even neighborhood—but not precise enough to find someone’s exact physical location.
What an IP address can reveal about a person
Tracing an IP address can give you useful information about a connection, including:
- Geolocation data like the country, city, or region where the IP is registered.
- Internet service provider like AT&T, Comcast, Vodafone.
- Network type, such as a home Wi-Fi network, mobile data, corporate VPN, or public hotspot.
- Whether it’s a static or dynamic IP address.
- Device and operating system (in some cases.
This level of detail allows websites to personalize content, helps businesses detect fraud, and even assists law enforcement investigations. However, on its own, an IP address doesn't identify individuals without additional context or data.
Why IP-based location data isn’t always accurate
IP geolocation is helpful—but it's not foolproof. If you've ever seen a website incorrectly guess your city, it’s probably due to:
- ISP routing: ISPs sometimes route internet traffic through central hubs, meaning you might appear to be connecting from a neighboring city.
- Shared IP addresses on mobile networks: Mobile providers assign dynamic IP addresses over large areas, making your IP-based location less precise.
- VPNs, proxies, or corporate networks: These intentionally mask IP addresses, making it seem like you’re connecting from another country or region entirely.
- Outdated geolocation databases: IP location databases might be outdated or incorrect, especially if ISPs frequently reassign IP addresses.
Geolocation limits and ISP masking
IP-based tracking relies entirely on your ISP’s infrastructure—not on precise, real-time location data like GPS. Your IP address only indicates the approximate area where your ISP has registered it, rather than your exact physical location.
Your ISP most likely assigns the same location to multiple users for efficiency, too. This makes it appear as if people in different towns are browsing from the same place. Corporate networks, university campuses, and cloud-based services further complicate tracking by routing internet traffic through central servers, obscuring the true location of individual users. All these factors combine to limit the accuracy of IP geolocation.
How ISPs assign and rotate IP addresses over time
Most internet users have dynamic IP addresses, meaning their ISP periodically changes their assigned IP to optimize network performance. This rotation happens in several ways:
- When reconnecting to the network: Restarting a modem or router can sometimes result in a new IP address.
- Automatically at set intervals: Some ISPs rotate IPs every few days or weeks, even if the user remains connected.
- When switching between networks: Using mobile data instead of Wi-Fi or connecting to a different network results in a new IP.
Because of this, long-term IP tracking is unreliable without additional data. An IP address used today might be reassigned tomorrow, making it difficult to trace someone consistently.
Legal and ethical considerations of IP tracing
Knowing how to trace an IP address can be valuable for security, fraud prevention, or troubleshooting—but it's crucial to stay within legal and ethical boundaries. Just because tracking an IP address is technically easy doesn't always mean it's appropriate. Laws vary by country, and the line between responsible IP tracking and a potential privacy violation can be thin.
Is it legal to trace someone’s IP address?
In most cases, yes. Checking an IP address to determine its general location or ISP is perfectly legal. Websites, businesses, and cybersecurity professionals do this routinely for security monitoring, analytics, and fraud prevention.
Things can get murky when it comes to how that information is used. Using IP addresses to track, harass, stalk, or reveal someone’s personal identity without consent can quickly become illegal. Privacy regulations like GDPR in Europe and the CCPA in California strictly limit how IP addresses and other personal data can be collected, stored, or used. To stay safe and compliant, always respect privacy laws and ensure consent when necessary.
When is IP tracking allowed by law?
IP tracking is legally acceptable—and even encouraged—in many situations. Businesses and financial institutions rely on it to prevent fraud, like when a bank flags a login attempt from an unusual location. Cybersecurity teams also monitor IP activity to detect hacking attempts, bot traffic, and unauthorized access. Tracing an IP to check where an email came from or spotting unknown devices on your home network is also totally fine.
Law enforcement agencies also use IP tracing to investigate cybercrime, but accessing detailed subscriber information from ISPs typically requires a court order or subpoena. ISPs won’t share private user details with the public, making detailed IP tracking limited to authorized agencies with proper legal backing.
Ethical considerations of IP tracking
Just because IP tracking is legal doesn’t mean it’s always ethical. Many websites and advertisers track IP addresses and use them to gather data about browsing habits for targeted ads, without users' explicit consent. While companies argue this improves user experience, it also raises significant privacy concerns, especially since most users aren't aware they're being tracked.
Another ethical challenge involves misidentification. IP addresses are frequently shared among multiple users—households, workplaces, or public Wi-Fi hotspots—which means tracing an IP address doesn’t reliably identify one specific person. This can lead to false accusations, wrongful bans, and unintentional privacy violations.
Ethical IP tracking should always prioritize transparency and consent. Users deserve to know when, how, and why their IP addresses are being monitored, with the option to opt out.
How to report malicious IP activity
If you encounter IP addresses connected to malicious activity, you should report it. Many ISPs and online platforms have dedicated abuse reporting systems, and flagging a harmful IP can help protect others from potential threats.
- For phishing or scams: Report to your email provider, which often offers a "Report Phishing" option.
- For cyberattacks or fraud: In the U.S., the FBI’s Internet Crime Complaint Center (IC3) handles online fraud cases. In the EU, report an IP to local data protection authorities.
- For large-scale threats like DDoS attacks and malware distribution: Submit the IP to AbuseIPDB, a public database that helps identify and block dangerous IPs.
How to protect your IP address from being traced
Your IP address makes you identifiable online. If you want to keep your browsing private and prevent unwanted tracking, you should protect it from prying eyes.
Why you should hide your IP address
Your digital address can expose you to targeted advertising, cyberattacks, or other potential risks. Hiding your IP helps you:
- Prevent online tracking: Websites and advertisers monitor IP addresses to build browsing profiles and serve targeted ads.
- Protect against cyber threats: Attackers can use IP addresses to launch targeted attacks or gather information about your network.
- Bypass restrictions and censorship: Changing your IP lets you use your online accounts on various platforms even if you’re traveling abroad.
How VPNs help prevent IP tracking
A Virtual Private Network (VPN) reroutes your internet traffic through a secure server before it reaches its destination. This means that websites, advertisers, and online services can’t see your actual IP address—they only see the IP of the VPN server. Since most VPNs have servers in multiple locations, you can appear to be browsing from a completely different region, making it difficult to determine your location.
While VPNs significantly enhance your privacy, they don't provide total anonymity. Logging into personal accounts or accepting cookies can still link online activities back to you. A VPN protects your IP address, but for maximum privacy, you should also practice good online hygiene.
Using ExpressVPN to boost your online anonymity
ExpressVPN is designed with privacy protection in mind. Its VPN server network spans 105 countries, making it easy to get a new IP address in the location of your choice. All servers operate exclusively on TrustedServer technology. This means they run entirely on RAM and not hard drives, wiping all data with every reboot so nothing is ever stored or left behind.
ExpressVPN servers use private, encrypted DNS, ensuring your browsing requests never leave the VPN tunnel. This encryption extends across all your traffic, protecting you from surveillance, hackers, and invasive monitoring. If your connection drops unexpectedly, Network Lock blocks internet traffic until the VPN reconnects, keeping your real IP address safe from leaks.
Beyond making it impossible for anyone to trace your IP address, ExpressVPN actively prevents online tracking. Its built-in Threat Manager blocks harmful trackers at the source, stopping advertisers and data brokers from building detailed activity profiles. Even your ISP can’t see which websites you’re visiting when you’re connected to ExpressVPN.
ExpressVPN is compatible with Windows, Mac, Android, iOS, Linux, and more, making it easy to protect your IP address on all your devices. It comes with a 30-day money-back guarantee, so you can try it risk-free.
Other methods to mask your IP address (Tor, proxy, mobile network)
While a VPN is the easiest, most secure way to hide your IP, there are other methods that offer temporary privacy—though each comes with drawbacks:
- Tor (The Onion Router): Routes traffic through multiple encrypted relays to mask your location, but it’s slow and often blocked by websites.
- Proxy servers: Act as intermediaries to mask your IP address but don’t encrypt your traffic, leaving data vulnerable to tracking.
- Switching networks: Gives you a new IP temporarily, but doesn’t give you control over the location of that IP.
- Public Wi-Fi: Offers a different IP address, but comes with major security risks, as hackers can intercept unencrypted traffic and steal your data.
Advanced IP tracing techniques
Learning how to trace an IP address using basic tools is just the beginning. Advanced techniques can offer deeper insights into online behavior, but they also raise significant privacy concerns.
How hackers use IP tracking for cyberattacks
Cybercriminals exploit IP tracking to identify targets and uncover network weaknesses. One of the most common methods is IP scanning, where hackers probe active IP addresses to find exposed devices or servers with security flaws. Once they locate a vulnerable system, they may launch brute-force attacks, inject malware, or exploit weak credentials to gain access.
IP tracking is also a critical tool in DDoS (Distributed Denial-of-Service) attacks, where hackers flood websites or networks with overwhelming traffic, rendering them inaccessible. Some cybercriminals use IP geolocation to create convincing phishing attacks, targeting victims based on their geographic location or internet service provider.
How businesses use IP tracking for marketing and security
Companies analyze IP data for legitimate business purposes, from customizing content and pricing to enhancing cybersecurity. Streaming platforms and e-commerce sites track IPs to adjust content availability and regional pricing. Online businesses monitor visitor IPs to optimize marketing strategies based on geographic trends.
Beyond marketing, IP tracking plays a major role in fraud detection and cybersecurity. Banks and online retailers monitor login attempts and transactions, flagging suspicious activity when an account is accessed from an unfamiliar IP. Corporate security teams also track employee logins to detect unauthorized access attempts, helping to prevent data breaches.
IP tracking in law enforcement and cybersecurity investigations
Law enforcement agencies regularly rely on IP tracking to investigate cybercrime, fraud, and illegal activities on the dark web. Authorities routinely request subscriber logs from ISPs to uncover suspects’ identities and locations.
However, knowing how to track an IP address effectively can be complicated when criminals mask their identities using VPNs, proxies, or the Tor network. In these situations, investigators use advanced methods such as analyzing metadata, obtaining historical records from ISPs, or performing traffic correlation to identify hidden connections. Even encrypted communications leave digital trails, allowing law enforcement to link anonymous online activities back to specific individuals.
Authorities also deploy sophisticated tactics like honeypots—fake systems designed to attract and trace cybercriminals—to uncover attackers’ real IP addresses. Through careful analysis of traffic patterns, timestamps, and network behaviors, investigators can often bypass privacy tools to track an IP address back to its original source.
Advanced IP tracking: packet sniffing & DNS analysis
Some tracking methods go far beyond basic IP lookups. Packet sniffing allows network administrators (or hackers) to capture and analyze internet traffic in real time. While IT professionals use it for security monitoring, packet sniffing can also help intercept sensitive data, such as passwords or private messages.
Another common technique is DNS analysis, which tracks domain name system (DNS) requests to see which websites an IP address has accessed. While cybersecurity experts use this method to detect malware infections, ISPs and advertisers also use DNS tracking to monitor browsing behavior.
FAQ—Common questions about IP tracing
Can I find someone’s exact address with their IP?
How accurate are IP lookup tools?
Can someone track my IP if I use a VPN?
What should I do if someone is tracking my IP?
Can IP tracing be used for cybersecurity investigations?
How do websites track my IP address?
Websites can also work with third-party tracking services that collect and analyze IP data for advertising and marketing purposes. Some websites take tracking even further by combining IP logging with browser fingerprinting and cookies. This allows them to build detailed user profiles and track browsing behavior across different sites.
How often do ISPs change my IP address?
Can I trace an IP address on my phone?
Can I track an IP address for free?
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN