IoT device management: Complete guide

Internet of Things (IoT) devices are everywhere today, from smart home gadgets to medical equipment. While a simple mobile app is usually enough to manage a few devices at home, things get far more complex when you’re dealing with hundreds or thousands of devices spread across sites, regions, or even countries.
That’s where centralized IoT device management platforms come in. They let teams monitor, update, and secure large fleets of devices from a single platform.
This guide focuses on how organizations can use these platforms to manage IoT devices at scale, with a brief look at what individual users can do to better protect their own smart devices.
What is IoT device management?
IoT device management is the process of remotely accessing, monitoring, maintaining, and securing devices connected to an IoT infrastructure. It usually covers the entire device lifecycle, from onboarding and configuration to maintenance through regular updates, followed eventually by retirement.
Most organizations use a central management platform or dashboard for this. It lets them oversee and control anything from a handful to thousands of devices at once, including sensors, gateways, and other smart connected hardware.
Learn more: To better understand how IoT devices communicate, read our guide on IoT connectivity.
Why device management matters for IoT
Done well, IoT device management brings several practical benefits:
- Faster device deployment: Remote onboarding and configuration help roll out new devices quickly, reducing setup time and letting businesses bring entire networks online almost immediately.
- Simplified access to devices: A single dashboard lets teams manage hundreds or thousands of devices across different locations, including hard-to-reach ones like those within mines, wells, streetlights, grain silos, or industrial tanks.
- Reduced outages and downtime: Centralized platforms let IT teams monitor, diagnose, and update devices in real time. They can spot problems early (like offline devices or low batteries) and send staff on-site when necessary.
- Enhanced IoT device security: Device management tools help apply encryption, segment devices, and enforce role-based access so only authorized users can view or control sensitive data.
- Efficient IoT device scaling: Automated registration and configuration make it simple to add more devices across offices, warehouses, intersections, or campuses without a lot of manual work.
- Lower hardware costs: Remote updates and predictive maintenance can extend device lifespans, helping organizations cut replacement and repair expenses.
What can individual IoT users do?
Most home users don’t need a full IoT device management platform. Instead, they typically manage devices through each vendor’s app or their home router’s admin panel. Still, there are a few simple ways individuals can improve how their smart devices are managed and secured:
- Use your router’s controls: Check which devices are connected, rename them clearly (e.g., “Living room camera”), and remove anything you don’t recognize.
- Keep firmware up to date: Turn on automatic updates where possible or check device apps regularly for new firmware and security patches.
- Segment your network: If your router supports it, put IoT devices on a separate guest or IoT network to reduce risk if one device is compromised.
- Consider a virtual private network (VPN)-enabled router: A VPN on a compatible router can encrypt traffic for all connected devices, including smart-home gadgets.
Core features of an IoT management platform
The exact features of an IoT device management platform depend on the vendor, but most centralized consoles have a common goal: to give organizations secure and efficient remote control over all their connected devices.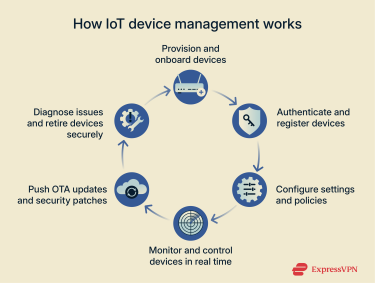
Device onboarding and provisioning
Onboarding and provisioning prepare a new device to join an IoT network. This usually includes:
- Registering the device
- Applying the right settings and policies
- Securely connecting it to the network
IoT management platforms can automate most of this work, so IT teams don’t have to configure each device by hand. Many platforms also support bulk registration, making it possible to onboard hundreds or thousands of smart devices at once.
Common provisioning protocols
To manage different types of hardware, device management platforms need to speak many “languages”. They typically support a range of IoT communication protocols so that devices with different chips and operating systems can still work together. These protocols are often grouped into three main categories:
- General-purpose IoT device communication protocols: Used for everyday device communication and management. They’re lightweight enough to run on resource-constrained devices and often support encryption when used with secure transport layers. Common examples include HTTP/HTTPS, Message Queuing Telemetry Transport (MQTT), which which can be secured when run over Transport Layer Security (TLS), and Constrained Application Protocol (CoAP), which can be secured with Datagram Transport Layer Security (DTLS).
- Equipment-specific protocols: Designed for industrial or building systems and specialized equipment. These are widely used in factories, automation, and building management. Typical examples include Open Platform Communications Unified Architecture, building automation and control networks, and Modbus.
- Low-power wide-area network (LPWAN) protocols: These are built for devices that send small amounts of data and need to run for a long time on limited power. They’re common in smart cities, manufacturing, precision agriculture, and smart lighting. Examples include Sigfox, Narrowband Internet of Things (NB-IoT), and long-range wide area network (LoRaWAN).
Lifecycle management of devices
IoT device management software supports both device provisioning and deprovisioning. When devices reach the end of their lifecycles, become obsolete, or are replaced, these platforms help IT teams decommission them securely and cost-effectively. They can safely remove or archive sensitive data, wipe configurations, revoke access credentials, and render any remaining information unreadable to reduce the risk of IoT vulnerabilities.
These tools also manage the day-to-day operational phase of a device’s lifecycle. They allow organizations to continuously monitor device health and performance and spot potential issues early. By identifying malfunctions before they escalate, businesses can avoid costly disruptions across their IoT networks.
Real-time monitoring and telemetry
IoT device management platforms allow administrators to remotely monitor, collect, and analyze device information in real time. Collected data can include device status, connectivity, and health metrics, as well as power usage, battery levels, signal strength, and operational anomalies. This way, organizations get the necessary diagnostics and data to perform predictive maintenance, ensuring minor problems don’t become major issues.
Many platforms also allow teams to set up custom alerts for critical events. For example, they can receive notifications when a device goes offline, when performance drops, or when unusual activity is detected. These alerts help IT teams react quickly and make time-sensitive decisions to prevent system or security failures, performance degradation, or data loss.
Remote monitoring techniques
Remote monitoring of connected devices generally involves using sensors on the devices to collect valuable data, such as temperature, humidity, vibration, location details, energy consumption, and other relevant metrics. The information is then sent to the centralized management platform for analysis using Wi-Fi, satellites, or cellular networks.
The central hub then processes, examines, and visualizes the gathered data using machine learning algorithms and statistical analysis. If the device management platform spots unusual data patterns or deviations from normal readings, it can alert administrators or take preconfigured actions, like powering off faulty IoT devices.
Remote configuration and updates
IoT device management consoles let administrators remotely adjust how devices behave. They can fine-tune settings and parameters, roll out new configurations, or add custom code to optimize features and adapt devices to changing requirements, without needing to physically work with each device.
Centralized dashboards also make it easy to push secure over-the-air (OTA) updates via Wi-Fi, cellular networks, or other wireless channels. IT teams can install manufacturer firmware updates, apply security patches, or update device software for an entire fleet at once, helping keep everything secure, consistent, and up to date.
Security in IoT device management
IoT device management requires strong security to prevent data breaches and critical system failures. Most platforms are designed with built-in protections against threats such as IoT botnets, firmware exploits, and physical device tampering.
They help organizations verify device and user identity, secure credentials, protect data in transit and at rest using IoT cloud security tools and encrypted communications, and ensure that only authorized devices and users can access the network, all while supporting compliance with relevant security regulations.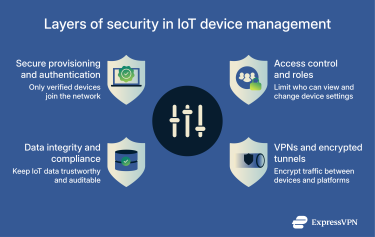
Learn more: To fully understand how connected devices and networks are secured, read our full IoT cybersecurity guide.
Secure provisioning and authentication
During the provisioning phase, organizations implement security measures to ensure that unsafe or unauthorized devices don’t compromise IoT networks and data. As part of IoT device registration and authentication, each device must have a unique, verifiable hardware identity, often established through cryptographic proof such as a device certificate.
In some cases, a device must also be linked to the correct user during provisioning. When manufacturers don’t know who the end user is, additional steps are needed to confirm authorized ownership during onboarding. This may involve asking the user to transmit a pairing code, scan a QR code, or press a specific button on the device.
Secure IoT device authentication then ensures that only trusted devices can connect to the network. This identity verification can rely on digital certificates, SIM-based authentication, encryption keys, or other mutual authentication mechanisms.
Access control and role-based permissions
IoT device management platforms rely on strong authentication methods, like unique passwords and two- or multi-factor authentication (2FA/MFA), to ensure only authorized users can manage connected devices. Access policies may also restrict what devices can access in the network, ensuring they only interact with approved resources, servers, and services.
Some platforms may even implement role-based access control, allowing organizations to assign and manage user roles with specific privileges. For instance, an administrator could create a support role that can view device details but not modify them or run troubleshooting commands.
Data integrity and compliance
Data corruption can occur due to cyberattacks, human error, or malfunctioning devices. It can put sensitive information at risk, disrupt critical services, and harm consumer trust. To avoid financial loss and comply with security regulations, like the General Data Protection Regulation (GDPR), organizations must ensure the reliability, accuracy, and security of data throughout the entire lifecycle of IoT devices.
IoT device management platforms support data integrity and compliance with built-in validation mechanisms, device authentication, and encryption. Many IoT solutions also integrate with compliance management systems, enabling real-time monitoring and automated policy enforcement to catch and address time-sensitive compliance issues.
VPNs and encrypted tunneling for IoT
Virtual private networks (VPNs) are services that encrypt internet traffic and route it through secure tunnels. Corporate VPNs and similar encrypted tunneling solutions can help protect data shared between devices, gateways, and centralized management consoles in IoT environments.
In enterprise deployments, IoT device management platforms typically integrate with business VPNs and device-security frameworks or rely on built-in encrypted tunnels. These tunnels help secure communication between remote sites (such as factories, warehouses, and branch offices) and the central network, protect traffic between IoT devices, gateways, and cloud-based management platforms, and hide internal network details from the public internet while still allowing controlled remote access.
By using corporate VPNs and encrypted tunneling in this way, organizations can maintain centralized control over large fleets of IoT devices while keeping sensitive operational and customer data protected in transit.
How VPNs secure IoT environments
VPNs help protect against various network-level IoT attacks by encrypting traffic. They mainly reduce the risk of man-in-the-middle (MITM) attacks, where malicious actors can try to monitor, alter, or intercept data shared between IoT devices. If successful, an MITM attack could allow cybercriminals to read unencrypted data shared between devices and cloud services, inject commands that modify device behavior, or remotely access and control IoT devices.
Additionally, organizations can use VPNs to segment IoT devices by creating isolated private networks. This approach helps enforce tailored security policies for specific device groups and contain potential threats within defined network zones.
Common VPN protocols for IoT
VPN protocols decide how VPN connections are established and how data is encrypted. Many protocol options are suitable for securing IoT connections, such as:
- OpenVPN: Provides strong security and broad compatibility, working on most mobile VPN apps and being widely used in both enterprise-grade and consumer routers.
- Lightway: Delivers high-end security and better speeds and reliability than traditional VPN protocols, like OpenVPN. It’s ExpressVPN’s proprietary protocol, available on routers and mobile apps.
- WireGuard: Maintains fast speeds due to its lightweight design while remaining secure. It’s supported by most mobile VPN apps but it’s not yet widely available on routers.
- IKEv2/IPsec: Offers fast speeds and stable connections and is commonly used in Android and iOS VPN apps, though it’s not supported on routers.
Best practices for efficient IoT management
As IoT ecosystems expand, managing connected devices efficiently becomes critical to maintaining stability, responsiveness, and data integrity. Here are the best practices to help organizations streamline operations and handle increasing workloads.
Ensuring scalability in enterprise environments
Many organizations struggle with onboarding, managing, and securing vast device fleets, often facing challenges related to security, connectivity, and infrastructure. Scalable management platforms that support automation are key to meeting this challenge. Centralized consoles often streamline essential tasks, including provisioning, configuration, monitoring, OTA updates, and decommissioning.
These platforms typically rely on cloud infrastructure, which scales resources dynamically and provides enhanced storage and processing capabilities for the large data volumes generated by IoT devices.
Edge computing integration
Edge computing is a distributed IT framework that processes data at or near the location where it’s generated by a device or sensor, rather than sending it long distances to a remote server. This approach reduces latency, network load, and input delay, improving real-time responsiveness. It also enhances safety and delivers a smoother end-user experience.
To gain these benefits, organizations should integrate existing IoT technologies with edge computing and ensure robust IoT edge device updates so that software, configurations, and security patches are applied consistently. This can be achieved through on-premise installations, such as IoT gateways, servers, and routers, or by using management platforms that include built-in edge computing capabilities.
AI in device management
Many platforms include built-in AI features or integrate with external AI models to enhance efficiency through predictive analytics, anomaly detection, and data visualization. Examples of AI in this context include smart home systems adjusting lighting based on user habits or industrial facilities predicting maintenance needs to minimize downtime.
Challenges and how to solve them
The growing scale and complexity of IoT deployments inevitably introduce challenges.
Device connectivity issues
Large-scale IoT deployments can lead to connectivity issues as networks become congested, especially in dense urban areas. This can increase latency, cause input lag, or result in dropped connections.
Problems also occur when many devices share the same Wi-Fi frequency bands, such as in apartment buildings or office complexes. In these cases, signal interference and limited bandwidth can affect performance. Similar issues appear in industrial IoT environments with large numbers of devices operating in proximity.
Solutions may include different IoT connectivity optimization methods, like using 5G cellular networks to improve coverage in smart cities or industrial areas, or adding offline modes to compatible devices (like LED lamps, for instance). Businesses can also use the LoRaWAN communication protocol to avoid concentrating IoT devices on crowded Wi-Fi frequency bands.
Interoperability between vendors
IoT interoperability refers to the ability of connected devices, networks, and systems from different vendors to communicate and operate together efficiently. However, not all solutions are fully compatible, and adding new hardware or software can sometimes create conflicts.
Compatibility issues often arise when IoT devices rely on different communication protocols or proprietary standards. Organizations can face integration difficulties where devices from multiple vendors can’t exchange data seamlessly.
To address this, businesses can adopt solutions that integrate well across ecosystems and use industry-standard communication protocols, such as MQTT and CoAP. Using a management platform that supports multiple device types from different vendors is also important, as it allows for seamless, vendor-agnostic onboarding.
Compliance and regulation obstacles
Regulatory compliance in IoT environments is critical because a single device vulnerability can potentially compromise the entire network. While IoT security standards exist, meeting them can be challenging due to the volume of requirements and the complexity of securing devices built from components supplied by different vendors.
Additional challenges arise when deployments span multiple regions, requiring adherence to different local regulations. Noncompliance can result in mandatory recalls, financial penalties, reputational damage, and restricted market access.
Organizations generally address these challenges by using device and compliance management platforms to automate regulatory adherence.
Real-world use cases
Public and private sectors, from hospitals and government buildings to factories and nuclear power plants, widely use IoT device management. Here are some common examples:
Healthcare device networks
Healthcare providers, hospitals, and clinics leverage device management platforms to securely onboard, monitor, and decommission essential medical equipment, such as wheelchairs, medication dispensers, IV pumps, patient monitors, wearable health trackers, and blood pressure monitors. Many consoles also provide real-time visibility and easy-to-audit tracking to support compliance with asset control policies.
Smart cities infrastructure
City officials and government institutions may use centralized consoles to control IoT devices that manage traffic and streetlights, public transit, solar panels, and waste management systems.
By analyzing device performance and planning maintenance, IoT management platforms can optimize public budgets. In addition, public safety agencies can leverage IoT for public safety to ensure faster emergency response times, implement smart surveillance and predictive policing, and improve resource allocation.
Industrial IoT (IIoT) applications
Different industries (manufacturing, agriculture, construction, or logistics) use IIoT devices, like actuators or sensors, to connect industrial machines to the internet. For example, they may use smart sensors to detect issues on conveyor belts or monitor mining equipment performance.
Centralized management platforms are also used to ensure machines are safely deployed and decommissioned, predict maintenance needs and optimize production processes, and reduce downtime. They can also help detect hazardous situations to lower the risk of environmental damage or injury.
FAQ: Common questions about IoT device management
What is an IoT device on my network?
An Internet of Things (IoT) device can be any smart home device on your network that connects to the internet and is managed remotely. Common examples include smart thermostats, lights, locks, refrigerators, ovens, mirrors, washing machines, vacuum cleaners, baby monitors, and pet finders.
How can I update firmware remotely?
Many consumer-grade Internet of Things (IoT) devices receive automatic firmware updates. However, more advanced or large-scale deployments often rely on centralized management platforms to remotely push simultaneous updates to connected devices.
Is IoT device management secure?
Not without the proper security measures. Internet of Things (IoT) device management requires strong security because devices often share sensitive data with each other. In addition, if an attacker compromised one connected device, it could put the whole network at risk. Organizations rely on centralized management platforms to secure onboarding and decommissioning, verify device and user identity, and encrypt communications.
Can I manage different vendor IoT devices in one platform?
In many cases, yes, as many Internet of Things (IoT) device management consoles support interoperability between devices from different vendors.
What are the best practices for monitoring IoT devices?
The best way to monitor IoT devices is to use a centralized console that collects real-time telemetry (status, performance, connectivity, and security events) from all devices in one place. Set up clear alerts for critical issues, like devices going offline, low battery, or unusual activity, so teams can react quickly. Wherever possible, combine cloud-based monitoring with basic checks at the edge, so essential monitoring continues even if connectivity is limited.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN