Managed DNS: Your complete guide to understanding and implementation
The Domain Name System (DNS) is a foundational component of every organization’s IT infrastructure. A reliable DNS service not only ensures fast query resolution and minimizes downtime, but it also strengthens resilience against DNS-based attacks.
Companies can choose to run their own DNS servers or outsource the function to a managed DNS provider. Managed DNS reduces the operational burden of running DNS in-house, but it also means giving up some control.
In this article, we’ll explain what managed DNS is, its pros and cons, and when it makes sense to use it over self-hosted DNS options.
What is managed DNS?
DNS translates readable domain names into numerical IP addresses so that browsers and applications know where to send traffic. In a managed DNS service, authoritative servers (one of the three types of nameservers) are owned and operated by a third‑party provider rather than by the organization that owns the domain.
The provider is in charge of DNS record management, answering queries, and working to replicate data across a global network. Outsourcing DNS means organizations can provide fast, reliable name resolution without having to maintain their own servers.
Managed DNS providers typically manage a global network that allows them to route users through the most efficient server for their location. Redundant designs allow for managed DNS to automatically route users away from slow or damaged servers to better-optimized ones with reduced latency.
Overall, managed DNS providers offer cost-effective long-term reliability, performance, scalability, and built-in protection against threats like distributed denial-of-service (DDoS) attacks.
How managed DNS works
When a user enters a domain name, their device sends a query to a recursive resolver. Recursive resolvers are servers that act on behalf of clients to answer queries directly from their cache or retrieve answers from upstream servers.
If the resolver doesn’t have the answer stored in its cache, it begins sending out recursive DNS queries, contacting other servers in the DNS system to locate the correct address.
The last stop in this process is the authoritative server, which holds the domain's records.
In a managed DNS model, the authoritative server belongs to the provider rather than the business itself. The provider replicates the domain’s records across a global anycast network, so user queries are answered by the nearest point of presence (PoP) for faster response times and reduced latency.
Providers also implement redundant servers, network architecture, and failover systems that detect outages and automatically redirect traffic to healthy servers. What’s more, some providers offer private, encrypted DNS to safeguard user data and protect internal users from surveillance.
Technical components of managed DNS services
Managed DNS platforms include several key components; below is a summary of the main ones.
- Global PoPs: These host the authoritative nameservers that answer DNS queries for your domains. They also run things like load balancing and failover logic to make sure queries are handled quickly and reliably.
- Primary and secondary servers: Primary servers store the main version of your DNS zone data (the master zone file), which is the set of resource records that define how a specific domain (or group of domains) is resolved and managed; secondary servers replicate this data through zone transfers to provide redundancy and ensure high availability.
- Anycast routing: This advertises the same IP address from multiple locations, directing queries to the optimal server node. This serves to reduce latency and offers some protection against DDoS attacks by distributing traffic across many servers.
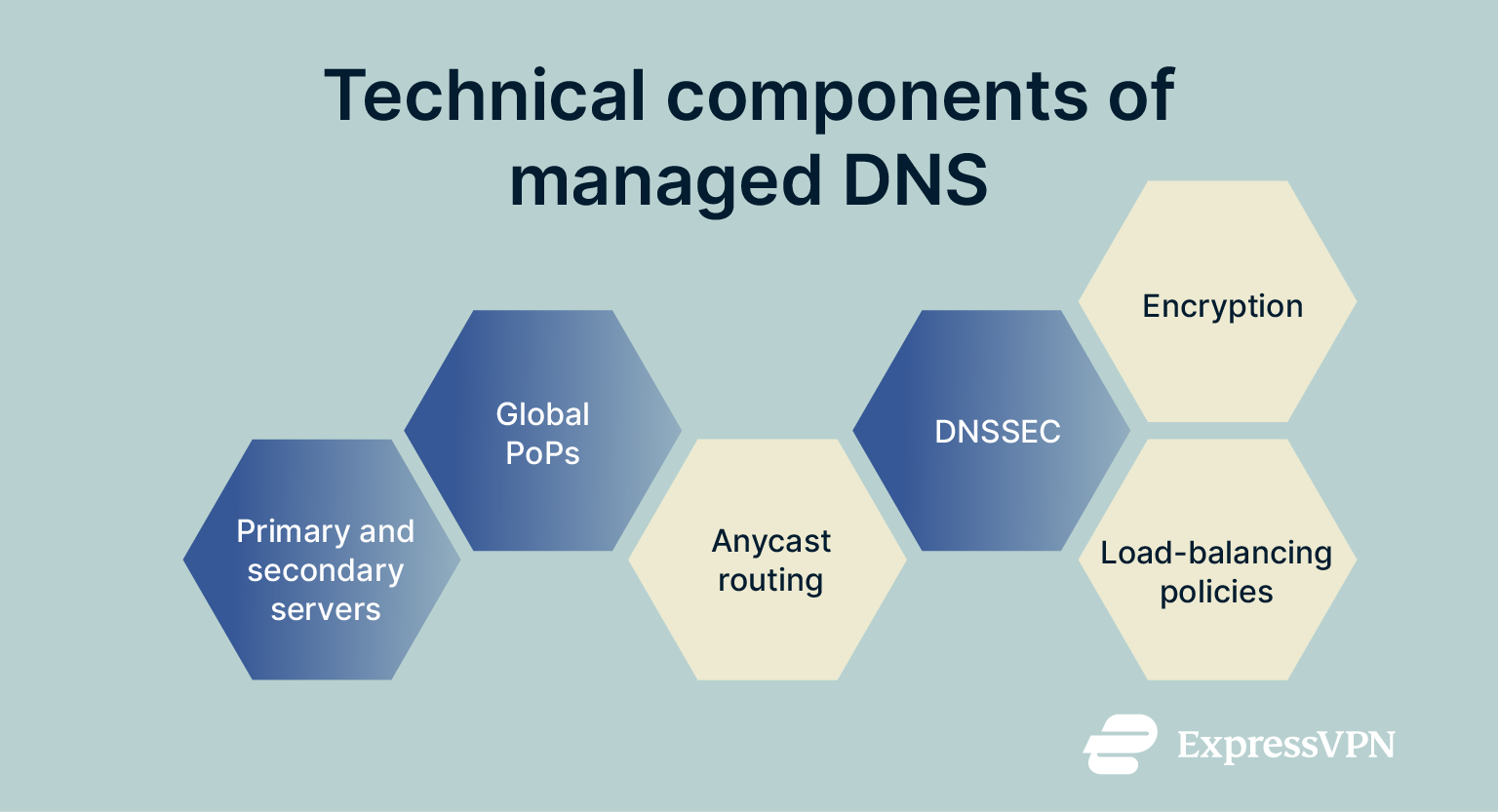
- Domain Name System Security Extensions (DNSSEC): This is a set of security protocols designed to protect the DNS from forgery, tampering, or spoofing. It adds cryptographic digital signatures to DNS records. The record holders can check these signatures to validate data.
- Encryption protocols: Encrypted DNS means that queries are sent over an encrypted connection, protecting them from interception or eavesdropping. Protocols such as DNS‑over‑TLS (DoT) or DNS-over-QUIC (DoQ) protect queries between clients and resolvers.
- Load‑balancing policies: These distribute traffic among servers, while monitoring and analytics provide visibility into query volume and performance. This offers two major benefits: users from regions around the world are directed to nearby servers for faster response times, and if one server is congested or facing high latency, automatic load-balancing reroutes users to healthy, responsive servers.
How to protect your data in managed DNS
With managed DNS, the provider is responsible for some aspects of security, but you’re ultimately still responsible for your own practices.
As mentioned above, managed DNS providers offer encryption protocols like DoT and DNS-over-HTTPS (DoH), which prevent third parties from eavesdropping on DNS queries in transit. Providers should also implement DNSSEC to prevent spoofing or tampering with DNS records. Additionally, reputable providers offer tools to block access to known malicious domains.
However, you should use your managed DNS dashboard to implement role-based access controls and enable multi-factor authentication (MFA) wherever supported. It's also important to enable logging and continuously monitor for threats, anomalies, or suspicious activity. Finally, make sure to perform regular audits to identify and address any vulnerabilities in your DNS configuration.
Managed DNS vs. self-hosted DNS
Managed DNS simplifies operations and provides global reach, advanced routing, DDoS mitigation, and real‑time analytics. It’s ideal for organizations with distributed users or limited IT resources.
Self‑hosting, on the other hand, appeals to those requiring full control over configuration, performance, and infrastructure. Both types of DNS have unique pros and cons.
| Feature | Self-hosting | Managed DNS |
| Customization | You retain full control over your servers, hardware, software, and policies | You have some customization via your user dashboard, but you can’t change server architecture |
| Performance | You must build your own server architecture; performance depends heavily on your infrastructure and network | Leading service providers use global PoPs, anycast routing, and redundant architecture for high performance |
| Cost-effectiveness | Predictable costs initially, but may become unpredictable due to maintenance, hardware failure, or scaling | Subscription fees that scale; however, costs can rise with traffic volume or added features |
| Ease of use | You create, manage, monitor, repair, and optimize your own servers; the process can be highly complex | The provider handles the technical aspects and provides a dashboard for accessibility; most providers offer customer support options |
| Security benefits | You’re responsible for implementing all security layers; self-hosting may offer more control and isolation, which some organizations prefer | DNS providers usually include strong security features by default; you have to trust them to implement and maintain them properly |
Pros and cons of self-hosting
Pros of self-hosting include:
- Control: Your organization maintains full control over what hardware, software, and policies are used.
- Low‑latency caching: Local resolvers can return answers in a few milliseconds, significantly improving the speed for internal users. However, if you're hosting authoritative DNS for public internet use, latency will depend on where your servers are located in relation to your end users.
- Customization: Self‑hosted environments support unique configurations and custom integrations.
- Price control: Since there are no per-query or subscription fees, organizations have more direct control over DNS costs. However, long-term expenses can be unpredictable because of the need for ongoing maintenance, hardware replacements, scaling, and staffing.
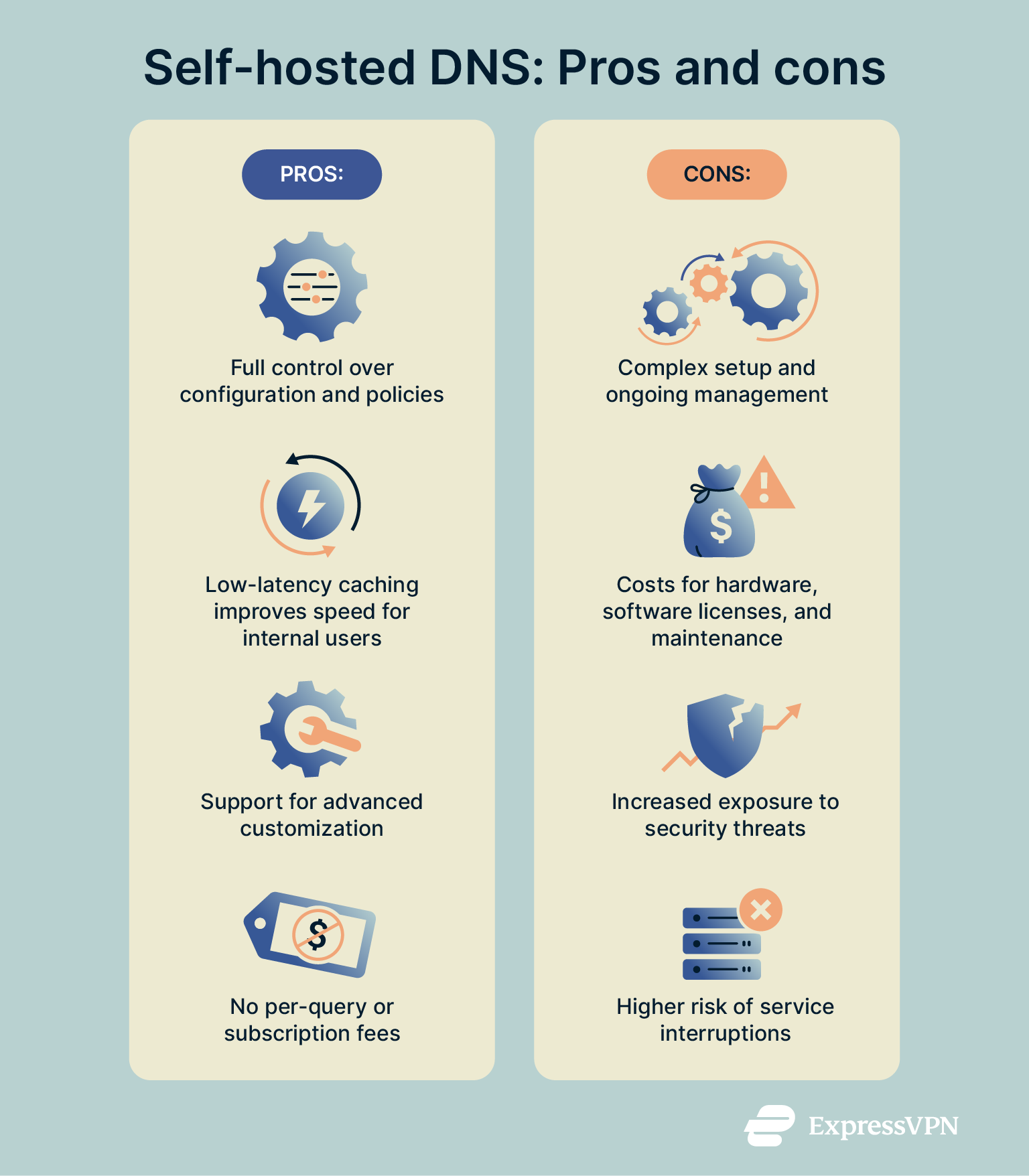
The downsides, on the other hand, include:
- Resource demands: Setup, configuration, DNSSEC management, and monitoring are significantly more complex with self-hosted DNS. These tasks require dedicated staff with specialized technical expertise.
- Cost: You need to factor in the cost of hardware, software licenses, and ongoing maintenance. Unplanned downtime can also be costly, often requiring internal resources to troubleshoot and resolve issues.
- Security risks: Self‑hosted DNS servers are vulnerable to threats like spoofing, cache poisoning, and DDoS attacks. Mitigating these risks involves implementing and maintaining complex security measures.
- Potential downtime: Without reliable failover systems, service interruptions are more likely. Downtime can disrupt access for customers, harm your reputation, and impact revenue.
Pros and cons of managed DNS
Managed DNS comes with its own, distinct set of advantages:
- Cost-effective: Managed DNS removes the upfront cost of hardware, maintenance, and data centers. Instead of building and managing your own DNS servers, you pay a subscription fee that scales with usage. This lowers the entry barrier and makes it easier for small to mid-sized companies to get reliable servers.
- Ease of use: Most managed DNS platforms include user-friendly dashboards, automation tools, and APIs that make adding, editing, or migrating records much simpler. You don’t need to manually configure zone files or manage system updates.
- Existing architecture: Providers operate globally distributed DNS networks using anycast routing to minimize latency and improve performance. This eliminates the need to build and maintain complex infrastructure on your own.
- Support: Managed DNS providers almost always offer some form of technical support, ranging from basic ticket systems to 24/7 enterprise-grade assistance.
- Integrated security and monitoring: As discussed above, many managed DNS services include built-in protections such as DDoS mitigation, DNSSEC signing, and encrypted DNS protocols. Real-time monitoring enables providers to detect issues early and reduce the risk of extended outages.
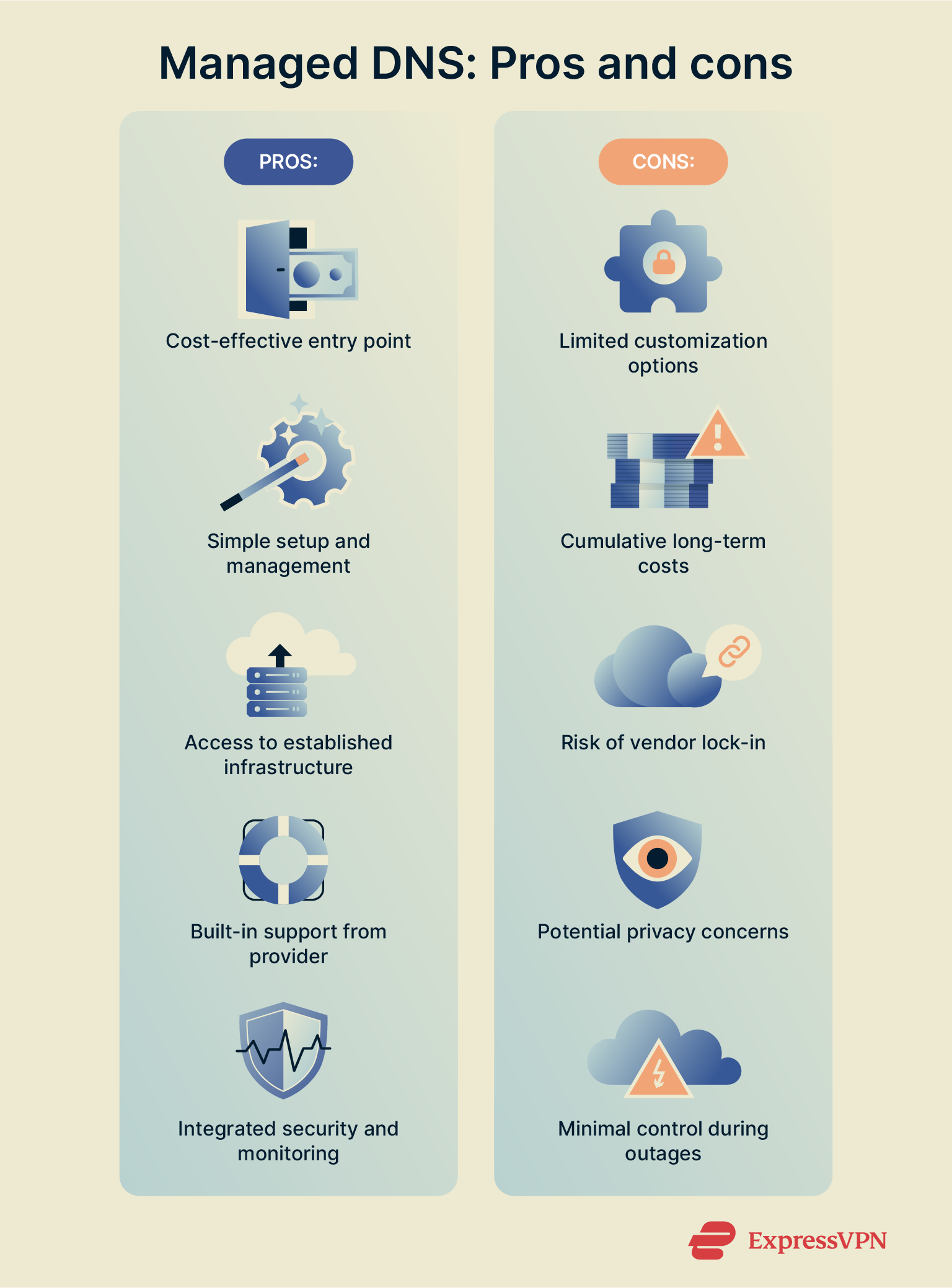
There are also several downsides of managed DNS to consider:
- Limited customization: Because the provider controls the underlying infrastructure, customization options may be limited. You may not be able to implement non-standard configurations or integrate with internal systems as freely as you could with self-hosted DNS.
- Cumulative subscription costs: Although managed DNS is cost-effective for many organizations, subscription fees can become significant at enterprise scale. Some organizations may need to upgrade to premium or dedicated plans to meet performance or compliance needs.
- Vendor lock-in: Relying on a single provider can lead to vendor lock-in, especially if the provider uses proprietary features or architectures that complicate migration. If the service becomes unstable or unreliable, switching can be costly and disruptive. Organizations can mitigate this risk with multi-provider strategies that replicate zone files and distribute traffic across multiple platforms.
- Privacy considerations: Using a third‑party service introduces privacy considerations. Make sure to review provider policies and choose vendors that align with your organization’s privacy and compliance requirements.
- Limited control over outages: Relying on a single provider introduces the risk that if your provider suffers an outage, you’ll be left to absorb the impact.
Which approach fits your business needs?
There’s no one-size-fits-all DNS solution; the right approach depends on your organization’s size, technical expertise, and risk tolerance. Managed DNS is ideal for businesses that prioritize simplicity, global performance, and built-in security. These services often provide higher uptime, automated features, and expert support with minimal infrastructure demands.
Self‑hosting is better for organizations that require full control over DNS operations, whether for compliance reasons, such as meeting data requirements under regulations like the General Data Protection Regulation (GDPR), or to implement custom logging, query handling, or internal policies.
Hybrid DNS setups are also common. Many organizations use managed DNS for public-facing zones and self-hosted DNS for internal networks. This approach adds complexity compared to fully managed services, but offers more control without the full operational burden of managing everything in-house.
Features to look for in a managed DNS service provider
When you’re choosing a managed DNS provider, weigh the reliability, security, performance, and ease of use that each provider promises. There can be great differences in what’s on offer, so breaking down providers’ strengths and weaknesses can help to guide your decision-making.
Core services offered by leading providers
Before you consider a managed DNS service, ensure it has the necessary core features to manage your queries safely. Look for the following features:
- Cloud DNS: Cloud-based DNS services are typically cost-effective and resilient. They leverage cloud infrastructure to provide high availability, low latency, and scalable performance.
- Traffic routing: This determines how DNS queries are resolved based on the user’s location and other conditions. A global provider should use a distributed network to route queries to the optimal server.
- Security features: Leading providers typically offer DDoS protection and DNSSEC to authenticate DNS records. Some also include protective DNS features to block known malicious domains associated with malware or phishing.
- Integration with other security solutions: Look for DNS services that support integration with your broader security ecosystem, such as security information and event management (SIEM) platforms, firewalls, and protective DNS filtering tools.
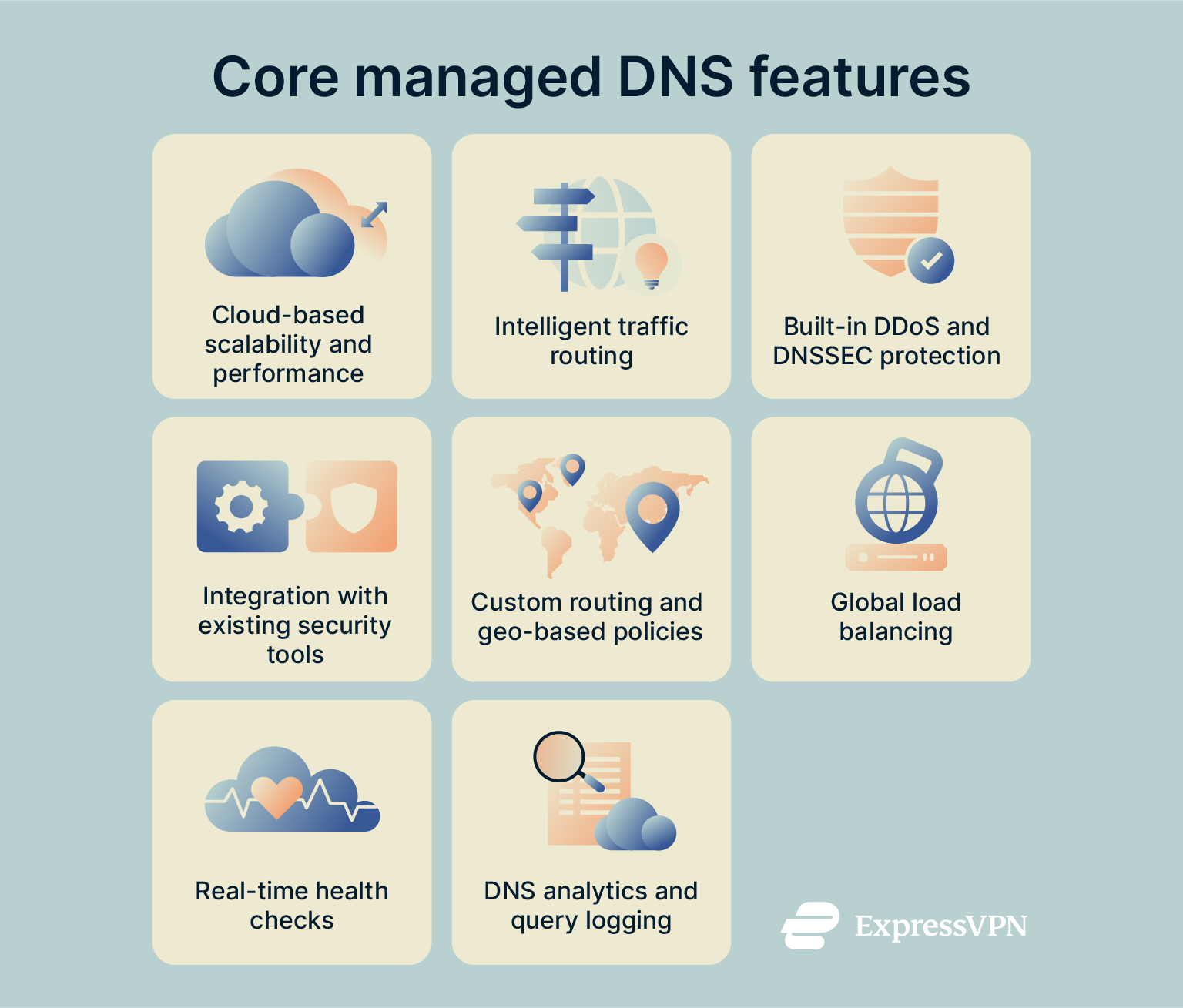
- Advanced routing policies: These policies let you control how DNS queries are resolved based on geographic location, latency, server health, or custom rules. This is typically only available with paid plans.
- Global load balancing: This distributes user traffic across multiple endpoints based on latency, server availability, or health. Without it, users may experience degraded performance or be routed to overloaded servers.
- Health checks: Providers should continuously monitor server health in real-time to find unresponsive servers or errors. Small errors in servers that build up over time can lead to extensive downtime and security vulnerabilities.
- Analytics: Look for user-friendly dashboards and query logs for visibility, troubleshooting, and forensics. Without proper monitoring tools, vulnerabilities and threats can stay hidden until customer complaints begin coming in.
How to evaluate performance guarantees
Before selecting a managed DNS provider, review their performance-related commitments carefully. The following criteria will help you assess whether they meet your technical and business needs.
- Network scope: Check how many PoPs the provider maintains and where they’re located. A larger, more geographically distributed network enables faster query resolution and reduces latency. It also enhances resilience and limits the impact of regional disruptions or attacks.
- Uptime service level agreement (SLA): An uptime SLA is a formal commitment that outlines the minimum level of availability you can expect, often expressed as a percentage (e.g., 99.99%). Make sure the SLA aligns with your business requirements, as any downtime outside the SLA may result in service credits but still carries operational and reputational costs.
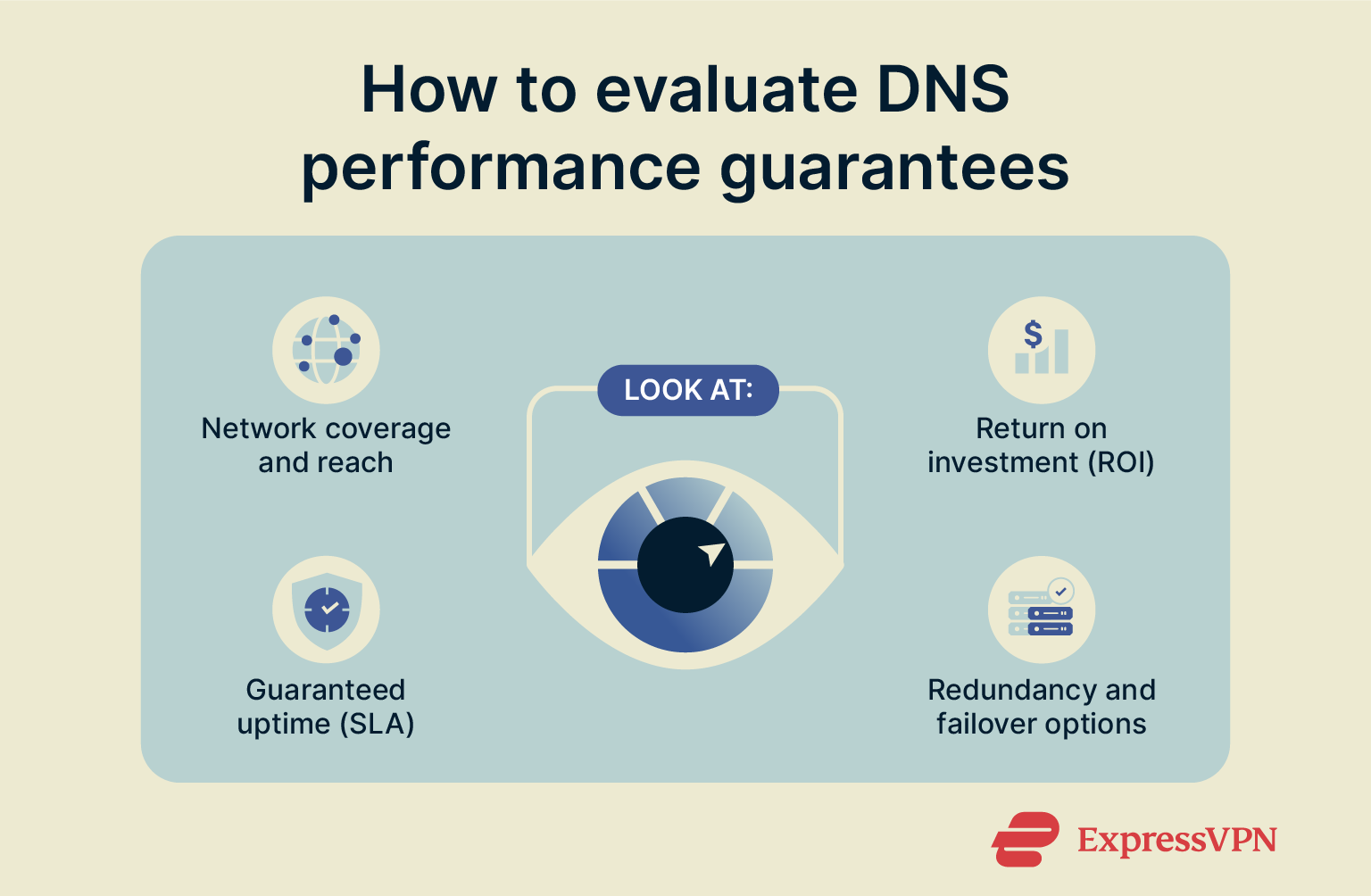
- Redundancy: Confirm that the provider has built-in redundancy, such as multiple data centers, anycast routing, and secondary server failover. These systems ensure that DNS queries can still be resolved even if one location or server becomes unavailable. Without redundancy, local failures can escalate into global outages.
- ROI: Consider how the provider’s performance commitments contribute to ROI. This isn’t just about uptime, but also fewer outages (avoiding lost revenue or productivity), reduced internal DNS management overhead, and improved security posture (lower incident response costs). If your current provider experiences frequent downtime or slow query resolution, switching to a higher-performing provider may justify the investment.
Free vs. paid managed DNS services
Free DNS services typically offer only basic functionality. They often have limited global coverage (few PoPs), minimal support, and they may impose usage caps. Some may also monetize the service by logging or selling user data.
In comparison, premium managed DNS services usually include:
- Larger, globally distributed server networks.
- Advanced routing and monitoring features.
- Stronger security protections (e.g., DNSSEC, DDoS mitigation, encrypted DNS).
- Higher guaranteed uptime (via SLAs).
- 24/7 customer support.
- Automated failover for resilience.
However, scaling costs can become a concern. Many providers charge based on query volume or usage tiers, which means costs can increase rapidly as your traffic grows.
For organizations with demanding performance or compliance needs, premium DNS services, which are often offered as high-availability, SLA-backed services, may be a better fit. These are designed for enterprises that require maximum uptime, low-latency global performance, and integrated security. But note that while they’re effective, they’re also much more expensive than basic managed DNS plans.
FAQ: Common questions about managed DNS
Who is managing my DNS?
Your Domain Name System (DNS) is either managed by your own organization or the company responsible for your domain’s authoritative servers. Third-party providers manage DNS infrastructure on your behalf, but still give you control over your domain settings.
How does managed DNS improve website performance?
Managed Domain Name System (DNS) services operate large, globally distributed networks of authoritative DNS servers. When a user makes a DNS query, the service automatically routes the request to the nearest or most responsive server, reducing latency and improving load times. These services also perform continuous health checks to detect and avoid unresponsive servers, ensuring high availability and fast resolution.
What are the costs associated with managed DNS services?
Managed Domain Name System (DNS) costs vary based on domain count, query volume, and included features. While free or low-cost plans exist for small projects, business-critical sites often require premium DNS options that offer higher uptime, better performance, and advanced security.
Can I switch from a managed DNS provider to self-hosting?
Yes, but before you do, it’s important to understand what self-hosting entails. You’ll need in-house expertise on configuring servers, implementing security features, and replicating zones across locations. You’ll also need to manage your own logs and keep up with health checks and repairs to prevent downtime.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN